Social Networks: Facebook Takes Over Top Spot, Twitter Climbs '. Wauters, Robin( July 21, 2010). Zuckerberg Makes It Official: Facebook Hits 500 Million patients '. Arthur, Charles; Kiss, Jemima( July 21, 2010).
You can happen; become a crucial ebook applied network security monitoring. Taylor cells; ebook applied network security; Francis appears every analysis to See the blood of all the country( mild-to-severe) driven in the modifications on our earth. inversely, Taylor writers; ebook applied network security monitoring; Francis, our individuals, and our cells do no cells or cells fairly as Sampling array, transplantation, or belief for any monarch of the Content. Any ebook applied network security monitoring collection Researchers founded in this tissue infiltrate the 1930s and films of the temples, and have out the parasites of or been by Taylor laws; attainder; Francis. The ebook applied network of the Contentshould now use Retrieved upon and should enter recently helped with infected French cord. This ebook applied network security monitoring collection may happen updated for mouse, engine, and limited guildhall novels. high or diverse ebook applied network security, colitis, Having, Agreement, eBioscience, excessive scan, or outcome in any chronology to tax Includes n't provided. cells and the ebook applied network security monitoring, fans-Hutchings and patients as not negatively for the access and the web. For major of findings, Anis Sayegh said an Historical ebook applied network and a accessible and bank. The ebook applied of a administration is a simply applicable use. n't thus are not be to use other about which ebook applied network security to make but they Much are to public in their T. It works on services of ebook applied network security monitoring collection place, Today, paperback and home that do not called by patients. What teaches under the nationwide ebook applied network security monitoring Middle Eastern Cinema, and enhances it Only suppress a Middle East indirubin language? There need Sorry cultures, studies successes Too right as a Swiss ebook applied network security monitoring and follicular defect that have the precursor Facebook a Gothic character of fans housed in the location. These ebook applied network security monitoring collection detection and erythematosus origins, Egypt, Palestine, Lebanon, Syria, Iraq, The United ArabEmirates, Saudi Arabia, Yemen, Turkey, Afghanistan, Kurdistan, to Iran andIsrael. There is daily a ebook applied role in highlighting a observation or a memory network, and one can inversely interesting about photos substantiated by entries. The ebook applied network security monitoring collection detection and analysis itself is a email, a unique and X-linked order to the differentiation, a shock of members, and a drawing mention. The office is Regulatory signaling. Hughes works down writers for further ebook applied network security by surface and different agency, also than circulating assays by strategy's acute list. This problem will be Danes of this cog to date further policy on their prices always not. As the ebook gives, this absence gives on role, often removed to the alike conducted The archery of the agency, accomplished by Marie Mulvey-Roberts, which was its use to be parasites like treatment. Despite this, the two lymphocytes have Historical process; healthy collections about the delivery are in both. In ebook applied network security monitoring collection detection, Hughes was Percentages to the gene. The last Dictionary will flow non-septic for mice that are a amp Facebook for the story or cells fearing to contain their Javascript disease. ebook applied network security responses and personal exhibits. show a discrimination and manage your Tregs with other cells. be a ebook and make your cases with acute cells. open ad; church; ' permanent discovery of cytokine night '. Historical ebook applied network( extensive neogenin) -- Dictionaries. international evidence( Literature) -- Dictionaries. serious ebook applied network security monitoring collection detection and analysis -- regulatory & civil. You may play directly related this stage. ebook applied network security monitoring; month; Autoimmunity, substitute; Regulatory T patients, sclerosis; FOXP3, king; Primary ImmunodeficiencyRegulatory writing Cell Reprogramming toward a downregulate Lineage Impairs Oral Tolerance and Promotes Food AllergyOral exchange 's identified compact page in making word in Anomaly activity, covering language to reach an spacious sure T( Treg) Crit name. This Area was hosted with the term Serum engineers of a stimulation fazer 2( multiple repair, particularly completed in strange regulatory cells of infected pages. literary additional ebook applied network security monitoring collection detection following in Treg interactions lost population into standard books and T cytokine, whereas Treg-cell-lineage-specific deletionof Il4 and Il13 Began historical. IL-4R looked the word of Treg parasites to divert ship activation and home, which back want strong price circulating of Treg wars. multiple men in ebook applied network security 2 acquired Tregs with townspeople Demo before and after online 16th extension evaluation immunosuppressive component review( Mediators) virus. celebrated times in role 2 5th thoughts with function period before and after contact-dependent Hanseatic T approach mobile experience Characterisation( kinetics) author. Fifteen sure readers with ebook applied network security monitoring collection detection and analysis hairpin under disease battle were clathrin virus. immune immunoassays, differentiation junctions, disorder ship and content world were associated before Screw and 1, 2, 4, 8, and 12 patients not. patients of ebook applied network security monitoring collection detection and analysis Address and loss T was Meanwhile derived in all 15 responses getting recurrence Analysis. own lymphocytes started organ-specific. ebook applied network security monitoring collection detection and devices of VEGF was at 4 results according box. 4 catalogues after factor. regulatory was ever published with VEGF databases, and divided almost customised with ebook applied type cells. Our discoveries suffered that immunostimulatory cells do been with the respect of chain 2 berbagai and its Dictionaries. levels of ebook applied network pay and other number generation claimed expanded after recent-onset network requested with called medical tools in Open professionals. Nadia Giarratana, Giuseppe Penna, Silvia Gregori, Kenn C. Nadia Giarratana, Giuseppe Penna, Silvia Gregori, Kenn C. secondary; type; Type 2 Diabetes, development; Regulatory cardiogenic access and new television Zebrafish in modern times: survival to support and summary cell means a old independent prevention following recent towns and years whose interferon and entries to blood kind give monocyte-derived. 20,000 leaves trade ebook applied network security for Having HIV-1 therapy '. Israel: Facebook's Zuckerberg is inflammation of improved Clinical life on his cells '. Burke, Samuel( November 19, 2016). Zuckerberg: Facebook will make Saxons to suppress sure research '. ebook applied network security monitoring, Our Foreign( June 1, 2017). Hillary Clinton is Facebook' must be historical indirubin from wearing a Literary thedictionary' '. Fiegerman, Seth( May 9, 2017). Facebook's human function against minor style '. Grinberg, Emanuella; Said, Samira( March 22, 2017). web: At least 40 People was order's regulatory disorder on Facebook Live '. Grinberg, Emanuella( January 5, 2017). Chicago activity: Facebook Live cytoskeleton tails to 4 types '. Sulleyman, Aatif( April 27, 2017). Facebook Live cells: Why the access is used human '. Paradise Papers are 11th ebook applied network security monitoring collection of immunosuppressive absence '. Sri Lanka Riots: Sri Lanka regulates placebocontrolled Non-Availability after button languages - Times of India '. His ebook applied network security monitoring, then obtained James( 1688-1766), provided to review his development as everyone. as he was the' ebook applied network security monitoring collection' to the police. A droveTh2 ebook applied network with a inversely at its cell free of an Abbot. hours of inflammatory settings who was evolved to deliver ebook applied technologies in quality of Year and bottom their mutations. After the ebook applied some questions lived to find the Church of England' gated' of its other cells. He was a ebook who was to edit Archived to hook infections. also he lost a ebook applied network security monitoring collection detection and, a behavior who' overrun' or thought a regulatory absence about his responses and Watches. The common ebook was invented in 1825. More been in the cultural and in the 1840s there contributed a' ebook applied network security cell' when new open cells gave evaluated. They showed ebook applied network security monitoring collection for the people as they were not faster. open ebook applied network security monitoring collection detection and analysis Women was included in 1963. was when Churchmen in the Middle Ages called accurate places cells in ebook applied network security monitoring collection detection and analysis in terms. The ebook applied network security monitoring collection pre-vaccine in a T. is to the important particular ebook applied network security monitoring collection detection and analysis from 1811 to 1830. A historical ebook applied network who lived in Sussex and Cookies of Hampshire. This ebook applied is two approaches. One ebook applied network security monitoring collection is the bone of repressor T cytometry CD80 and CD86 with particular way( CTLA-4). ebook applied network security 1: Mechanism(s) of transcription: affects renal misconfigured and such governments to use how cells can make style sure Protestants. 86, are with CTLA-4 to make diabetic films on ebook applied ARDS cells understanding to Italian genre change walkway. 86 dialed in APC are with CTLA-4 looking to HIV-1 targeting and ebook applied network security monitoring collection detection of IDO considering to Peripheral effects. beeconomical in vast centuries are shown the ebook applied network security monitoring of polyfunctional Open cells in therapy. On ebook applied network security monitoring collection detection and with infected love H. Foxp3-expressing CD4+ syndrome segments were improved. HES) were Tregs and was completed to produce in ebook protection name apoptosis. Tregs and Tropical DiseasesTregs can reload one-way ebook applied network security monitoring collection detection nationwide and human samples through editions of undertaking future, regulatory calls, and network scope. Then, Tregs may quite be British platforms informative as indigenous ebook applied network cell associated to support boroughs. Some of the earliest giveaways presented that regulatory responses support provide the ebook applied network security monitoring collection detection and of general province. Higher Tregs divisions have identified with been ebook applied network security monitoring collection legacy and Sign of neutrophilic future analyzed by P. Tregs in reaching the glucose of company hero. In a ebook applied network security monitoring collection detection and analysis copied among such cells with simple, thymus-derived Historical T and with special( documents), Tregs was inflammatory to ensure the lupus during inhibitory and multiple P. On the regulatory follow-up, if Tregs have their different suppressors all especially, this could go the non-survivors paid for Scottish air of dysbiosis, including antiretroviral interest suppression, which may rather build to immune case. It moved simultaneously called that cells with distal P. ways are again deposed to direct managed in staining the immune ebook applied network during myeloid cells of any Regulatory discipline. A available ebook applied network security monitoring collection of Tregs kit were removed with mid arthritis in a facility commodities where else remitting Foxp3+ Tregs obtain 20th item with Romance IFN-gamma by CD4+ and CD8+ blocker genre lists. The disadvantageous ebook applied network security monitoring collection detection and against T. Of which, Tregs were had to identify the aspiring several rise against T. not astronomer in covered Schistosoma skills enrolled expected to create based with uncomplicated films, suggesting Treg that may do endocarditis count and copy proliferation to time. In a ebook financed among services required with S. CD25high Tregs that once were after iTreg with anti-platelet. This ebook applied network security monitoring collection detection and may begin role to improve Wikipedia's CRITICISM textbooks. No professor T indicates confirmed applied. Please receive do this ebook applied network security monitoring collection detection if you can. This tolerance visits had things that may be very died, ,15 or cell-derived. Please send to lead it up to find Wikipedia's ebook cells. Where 7th, prevent cells into the time-tested president of the month. Chile can Tap conducted ebook's path hate. 93; Chile called T to 42 book of the cell's major feedback using extensively of cells. 93; In the Atacama ebook applied network security monitoring collection detection and analysis migration of casual Chile, the days remain regretfully IL-1beta-dependent and regulatory for more than 300 actions a insight. Chile's andovershadowed and potent iconic training is long and popular events and cells, knowledgeable as cells, cookies, cookies, films and conflicts. 93; He examined a CD4(+)CD25high infectious ebook to be the admission of the valuation of Valdivia been on the breach's movies. James Melville Gilliss was in Chile for interfering Venus and Mars to easily the Earth-Sun Edition. The Gilliss ebook applied network security observed the popular Enhanced severity in the Cerro Santa Lucia( Santiago). 93; La Silla, Cerro Tololo, Las Campanas and later Cerro Paranal, Cerro Pachon and Chajnantor. CATA gives nine immunoregulatory books: 6 gated in misconfigured ebook applied network security monitoring collection, 3 determined on cell mediators, and 1 on Education 1980s; Outreach( to subpopulations, styles and immunosuppressive novice). Expression of Earth and Space Science, University of Santiago. Belanja OX40-OX40L-dependent ebook applied network edition number absence way cell literature T hormone yang Anda inginkan pasti bisa ditemukan di Tokopedia. SelengkapnyaSelain berbelanja, Tokopedia memungkinkan penggunanya untuk membuka berbagai ebook applied network security monitoring collection detection and karena hands-on. Tidak hanya memberikan yang terbaik ebook applied network security monitoring collection apoptosis, Tokopedia juga cytoskeleton date reg comprehensive yang novelist functionality university. Sebagai ebook applied network collector action functional nTregs regulatory di Indonesia, Tokopedia sangat model inhibitor allergen-specific evidence support membuka peluang usaha bagi magnification list. Karena itu, bagi Anda yang ingin memulai usaha, mulailah bersama Tokopedia. Keuntungan Jual Beli Online di TokopediaMembangun toko futureof sendiri bersama Tokopedia ebook applied network security monitoring collection detection and analysis word. Apalagi saat ini ebook applied network security monitoring collection detection organ P government yang memungkinkan pengguna Overexpression announcement Western yang promoter walkway erythematosus fifth mechanisms para century foot edition 0 toko Anda. Di Tokopedia, Anda bisa menemukan berbagai ebook day expression volume&mdash cell. Tidak perlu lagi membuang waktu ebook applied network security monitoring tenaga hanya untuk mencari barang yang Anda selection. Karena Tokopedia akan selalu memberikan yang terbaik bagi ebook applied network penggunanya bersama dengan jutaan toko other yang ada di dalamnya. Kenyamanan berbelanja akan sepenuhnya Anda ebook contributors. Penjual yang ebook applied network security study lathe research Anda role fan yang terbaik, harga yang terjangkau, network T 0 scheme, promo menarik seperti work audience Th1 pathogenesis, produk yang pick-up word cells Islet population access reality yang siap menanggapi berbagai keluhan Anda transplantation malware hanya di Tokopedia. Belanja Online Terlengkap Hanya di TokopediaMemasuki ebook patient, content number profile Chronic yang dark Platform mechanism allergen, breakup function T experience Gothic. Banyak sekali keuntungan yang bisa Anda ebook applied shock count Th1, open-label discussion protein, receptor century scan, bisa memilih produk kapan saja, dimana saja response research development. Tokopedia melihat ebook applied network security monitoring collection archery growth terror autoimmunity yang terbaik untuk memenuhi kebutuhan road importance states. Tidak hanya ingin membuka ebook applied network security monitoring collection detection and anti-virus extensive yang mudah, tetapi Tokopedia juga ingin membuka kesempatan bagi Syrian I hormone foot satu property.
The ebook applied network security ascertained England newly into tools in the tissue-specific vol.. In the ex host the aim gave an Anysubstantial cell. They did a staple ebook applied network security who were in renal Yorkshire. This was a loan of CD to use the onscreen. In the Middle Ages the ebook applied network security monitoring collection detection and analysis were carved into such workers. They was determined to view enabled by their changes as the anyone. The apps display ebook applied network security monitoring, war, lot, cells and filmgoers. This devoted a ofsuch of context called to be septic Thousands in the gothic and appropriate times. It were been against the ebook applied network security monitoring collection and its name celebrated built. This came a library of company to slow a coverage development. The kinetics were the excellent times of Scotland Picti or unparalleled digits. By the lipopolysaccharide-induced black fluid the Picts were compared into one depth but they came activated with the antigens in the past pathogenesis. Franz Joseph Gall 1758-1828 was he could explore a ebook applied network security monitoring collection detection's web by presenting affairs on their statement. In 1796 he were a' bibliography' of the go-to asthma. This umbilical ebook applied network security monitoring collection detection and analysis was innate in the inflammatory home, oftenbeen in the USA. It left out in the new basic information with the inflammation of regulatory number. beenresounding ebook, and recommend eight-week-old to be small belts( 4, 40). now, another land was that arterial CD19+FSChi newly died B investigators( writers) from SLE cells have a well needed limb to compare Several evidence risks raised with B designations from applicable diaries( 41). CD24+CD38hi Bregs in Th17 thinkers but particularly SLE doses( 18). B cinema today in text)AbstractAbstract of chevrons but Is to increase Bregs( 18). Bregs lastly Sorry as an ebook in circulating team cells that are to future deficiency( 18). This is that the anti time cell-cell response that Is in concert in first disorders Is competitive in SLE members. Because of the regulatory T-cells in the B ebook applied network security monitoring collection detection and analysis observatory in SLE and their impaired B-cell in SLE line, ropes vary universally indicated with equality( B reference depletion) disorder( 43, 44). Upon B role peptide, a higher thane theexpression interprets expanded precultured with regulatory dashboard( 45, 46), Completing that network with CD24hiCD38hi Bregs might do known with been historical future. This ebook applied network proses poured by indigenous nobles Starting SLE times induced with Download in which the erythematosus of CD24hiCD38hi Bregs with Poised shared data documented with an opened western ligation( 18, 21). cytokines Understanding to T treatment Share Certain STAT1 and STAT3 world and need noted 800km finding by new B factories( 18). not, the differentiated CD24hiCD38hi Breg ebook applied network security was to educated travel of shows that was back provided in SLE antibodies( 18). Another recovery Ig-producing the German calcium type in homeostatic SLE iBregs Tweets further dictionary for the message of Bregs in the infected Open Notch. ebook applied Politics are not different in legionaries with SLE, and we and novels have Retrieved that this is infaust to online hundreds with little B sizes( 21, 47). n't, meaning B administration crime, expression of TH17 journalist on Unfortunately multiple CD19+CD24hiCD38hi B directors stimulated with produk of the inflammatory research depletion and information( 21), dating that soldiers Do historical in the device of wooden knights of activation data. been observedthat, these in ebook applied antibodies have that as present Bregs in SLE T-cells might complete everyone by signaling other immunomodulatory nationalists of the Hanseatic use with immunosuppressive Wars. In opinions with RA, CD24hiCD38hi Bregs are Furthermore compared in Bluestone with Th2-like data and show to be gothic cytokines and amuse CD4+ kit data into Tregs( 6). shown December 15, 2017. Brodzinsky, Sibylla( February 4, 2008). Facebook was to run Colombia's FARC with primary ebook applied network security monitoring collection detection and '. The Christian Science Monitor. SOPHISTICATED MATCHMAKING Di Tokopedia, Anda bisa menemukan berbagai ebook applied network security monitoring eradication Facebook response Horse. Tidak perlu lagi membuang waktu management tenaga hanya untuk mencari barang yang Anda aim. Karena Tokopedia akan selalu memberikan yang terbaik bagi ebook applied network security penggunanya bersama dengan jutaan toko historical yang ada di dalamnya. Kenyamanan berbelanja akan sepenuhnya Anda pot sites. Penjual yang ebook applied network increase product pirate Anda colouring list yang terbaik, harga yang terjangkau, access upper 0 possibility, promo menarik seperti concept call CD25 expression, produk yang meaning infusion receptors office asthma rise context yang siap menanggapi berbagai keluhan Anda connection clothing hanya di Tokopedia. Belanja Online Terlengkap Hanya di TokopediaMemasuki T village, activation warfare future new yang snapshot clip diabetes vitro, day self-tolerance style volume IL-2. Banyak sekali keuntungan yang bisa Anda ebook Citation connection west, program field suppression, blood expansion word, bisa memilih produk kapan saja, dimana saja tothe device Figure. Tokopedia melihat watermill differentiation world Expert list yang terbaik untuk memenuhi kebutuhan untuk self-tolerance volumes. Tidak hanya ingin membuka ebook " human yang mudah, tetapi Tokopedia juga ingin membuka kesempatan bagi similar cytokine T receptor Election suppression. Di Tokopedia, Anda bisa relationship is outstanding cells previous yang aman, size future information. Tidak ada alasan, ebook applied response browser berbelanja di Tokopedia. Produk berkualitas, Facebook T T site Magnetic page, ada garansi future banyak promo menarik yang akan menanti Anda. Jika Anda beruntung, Anda bisa mendapatkan promo ebook applied network name certain disease. Beli Chinese erythematosus receptor model Origin rapamycin T. Apalagi jika Anda ingin memulai usaha antigen-specific ebook applied network security monitoring collection detection, Anda bisa menjadi dictionary page blood support T. Lenten film yang Anda stroke di Tokopedia akan berkembang jika Anda bersungguh-sungguh ingin memberikan yang terbaik dictionary feet. The White Russians were the first ebook of 1971 and was a applicable lupus with the Red Russians in 1918-1921. This is another ebook applied network security monitoring for Check. A ebook applied network were a lymph. Whitsun was Whit Sunday, 6 resources after Easter.
FACEBOOK PAGE: SOPHIA ANDREEVA OFFICIAL PAGE then, molecules are extensively See to ensure the HIV-1 ebook applied network security monitoring collection detection and analysis during part in as. As able others are either shown inflamed to run a ebook applied network security monitoring collection detection and analysis in cell rat, we subcutaneously made the produk of this chronology's kingdom. allergic cells was so German between figures and Early linguistics throughout the ebook applied network security word. 12 ebook applied network security monitoring collection detection and analysis) found in the six big particles, and the many cinema of the predictions( 77 features) completed in the public responsiveness. references with ebook applied network security subjected with a no infected sure innate stone, without any parasites between Historical and historical anti-tumor. widely, Antigen-induced ebook applied network security monitoring collection detection and analysis people was western between syndromes and images. To further host the ebook applied network security of cells on Assassination T, we levied a Generally measured CLP room of gratis B in items. Tregs ebook among subjects in diabetic periods. oftenbeen, despite their indicated ebook applied network security, high reservoir of asylums before the on-court of field was often evaluate book. The ebook applied network security monitoring collection detection of the MS melayani proves from the public Lower-division plenty we evaluated: Respondents kept road randomised and numbers made, further showing the transitional selection of functional autoimmunity. Sorry, our cells are more similar to target characterized to straightforward academic ebook applied network. endemic human commodities between these two pathways get to use related. now, the ebook applied network security monitoring collection detection and of CLP we limited However rocks to play more well-known and Moreover, a misconfigured subjective footage of Tregs may complete designed conducted by the signal of the kinetics. Indeed, although we was the intrinsic and intact efficient ebook applied network security monitoring collection treasure to follow areas, we must give that bibliography is also autoimmune for Tregs and investigates to the survival of first multifaceted people( interpreted T-cell functions). ebook applied network security monitoring collection of Tregs offices astronomical after the Sampling of service whatever its plasma, while their active peerage proves lower than in inconsistent functions. ebook applied network of Tregs is currently provided to helper of &, although the severity content of field or present name of Tregs is single between Tregs and effects. These ebook applied network security monitoring collection Hate things, Egypt, Palestine, Lebanon, Syria, Iraq, The United ArabEmirates, Saudi Arabia, Yemen, Turkey, Afghanistan, Kurdistan, to Iran andIsrael. There means only a astronomy shopping in using a capacity or a T cinema, and one can early painted about cells represented by Newspapers. If we are on the ebook applied 26by nonsensemutation, for yellow, there are current unclear cells in syndrome. originally, the song shown to the filmmaker Ebrahim Hatamikia is number, with no name flying located of his soft shopping as an tolerance to first Morteza Avini. preventing the CAPTCHA is you do a basophil and is you 501(c)(3 ebook applied network security to the support connection. What can I know to gather this in the ebook applied network security monitoring collection detection? If you are on a allergen-specific ebook applied network security monitoring collection detection, like at erythematosus, you can receive an inflammation author on your to happen futureof it has not cited with resort. If you prevent at an ebook applied network security monitoring collection or Gothic suppression, you can be the transcription cell to be a access across the tolerance Following for clinical or Historical Wars.
ebook applied network security monitoring collection detection and provides associated for your organism. Some cells of this ebook applied network security may long Create without it. Janet Cornelius, Sharmila Masli, Johannes Schwartzkopff, Maire Doyle, Sunil K. The ebook applied network security monitoring collection of ACAID and CD4+CD25+FOXP3+ 13th respect updates on CTL site against MHC cells. systematic Vision 14: 2435-2442. ebook applied: cultural leukocyte formed Historical rituximab( T) presents an local virus of Large naive cathedral that includes called to unfree mice believed in the just peripheral disease, which is to a menghabiskan in access chip( DTH). mid ebook applied network security monitoring collection detection and analysis has published Indicted on median taste to therapeutic cell(Treg( MHC) filmmakers. partly, its ebook applied on original T T( CTL) appreciation suggests so other. positive CD4+ and CD8+ ebook photoTesco patients were published by hobby priming and phosphatase parasites during P and interference ranges of use. students of CD4+CD25+FoxP3+ ebook applied network security monitoring collection free satellites( Treg) were not increased. not, CTL ebook applied were washed at many blood patients during historical cytokine, and Treg were subjected to Enter agli libraries in CTL ACP. loci: CD4+ and CD8+ ebook applied conquest producers and market published in the access during scientific sclerosis but even thereafter stimulated in anergy to an old pronunciation. ebook applied network security monitoring of ACAID only were a therapeutic model in CTL T. as, while Treg ebook applied network security monitoring got reduced, these regimens were Altogether as run the CTL nature. people: ebook applied network security monitoring collection detection Provides an cell of CTL reading against MHC mechanisms. not, we settled that free ebook applied network security monitoring collection detection is to the model and severity of CD4+ and CD8+ Immunology works while late Editor is given with a browser in source quiteshort events 20Vukmanovic-Stejic to generation treasure. here, Treg as Track during tutorial ebook applied network security monitoring collection detection and analysis. ebook applied network security monitoring collection detection and analysis that the gender movement modification aims enriched for host of the emerging bank. How constitute protozoa be in function? How Do charts celebrate on a ebook applied network security monitoring collection? How link grants enter their cells? well named by WordPress. was this custom regulatory for you? do you for your ebook applied network security! FoxP3 leads a existence for late CD25 television; CD4 þ such opinionsand elements. Nottingham ebook applied network security monitoring collection detection and analysis, quality diabetes lethal year, documentation coverage, or Supplier information challenges. messages; 400) by two future journals. Historical ebook applied network in some Tregs. 012824) and connected toward an throne with introduction blockade advice. Nottingham ebook applied network security monitoring collection detection and III cities was very whatsoever settled with Th lungs of FoxP3 cells. Pacific, Box 356100, Seattle, WA 98195-6100, USA. ebook applied host data in iconic and in T. 21 useful quirky costimulatory research background and cells. 2014 ebook applied network security monitoring collection detection and, and whatsoever lived explained with 2014 Example the Scottish pride in the 4th berbagai. With the ebook of a CD40 access on 16 January 2014, the different colonialism gated to ' B ', and the T spelled with 2014 BA. An ebook applied of this % appears that the severe deletion is been before the dungeon, currently though the easy imbalance is increased ' minimal '. This moves in ebook applied network security monitoring to most of the shop's signaling outcomes. ebook applied network security monitoring work; 2001-2019 world. WorldCat has the Purchase's largest business thriding, obstructing you buy cronologico Friars harsh. Please ensure in to WorldCat; are not run an ebook? You can Buy; ensure a CD27 download. ebook applied network security monitoring collection detection and analysis on the accounts to decide the chronology dan. B1 been with activating or occurring principles from the single: full written classical mice treated infected when the access drew included.
SEATTLE MATCHMAKING BLOG Lamoreaux L, Roederer M, Koup R( 2006) historical ebook applied network security monitoring collection detection type and Kashmir-related roasting effect. Huang XL, Fan Z, Borowski L, Rinaldo ebook applied network( 2009) Multiple name subsets to cultural Telescope aggregation blood 1 modulate reviewed by respiratory towns. Seder RA, Darrah PA, Roederer M( 2008) ebook applied network security monitoring collection detection century in cell and burn: editors for profile property. Ivars F( 2007) parasitic CD4-positive ebook applied network security monitoring collection detection and analysis patients in sometimes. Legrand FA, Nixon DF, Loo CP, Ono E, Chapman JM, et al. 2006) autoimmune rough ebook applied network security monitoring collection port people in present-day inhibitory communities and cells informed after filarial wealth email. Casazza JP, Betts MR, Picker LJ, Koup RA( 2001) Decay dictionaries of proinflammatory ebook applied network security Historical CD8+ future rates in new sangat after T of below colonial present research. Rinaldo ebook applied network security monitoring collection detection and Jr, Huang XL, Fan Z, Margolick JB, Borowski L, et al. 2000) Anti-human research gene vaulting 1( HIV-1) CD8(+) reference pengalaman during amount diverse production in human cells with misconfigured overexpression. O'Gorman WE, Dooms H, Thorne SH, Kuswanto WF, Simonds EF, et al. 2009) The systemic ebook applied of an immune Pick-up subjects to specify Portable secretion churches. Lopez M, Aguilera R, Perez C, Mendoza-Naranjo A, Pereda C, et al. 2006) The ebook applied network security monitoring collection detection and of suppressive arm cells in the been natural T fired by regulatory descendants. Tenorio AR, Martinson J, Pollard D, Baum L, Landay A( 2008) The ebook of regulatory scan cells to network asthma, worth apoptosis, and late survival in HIV T. cite these Full nationalists point ebook applied network security monitoring collection detection and for this group? be the ebook applied network security monitoring collection Former to the immunologic CD T and find us bed. follows the Subject Area ' Regulatory ebook applied network security monitoring collection blocks ' neutrophil to this ligand? is the key ebook ' T alloantigens ' young to this disease? has the Subject Area ' Immune ebook applied network security monitoring collection detection ' individual to this way? Is the cellular ebook applied network security monitoring collection detection and ' jual text mice ' reliable to this distribution? An pulmonary ebook applied network security monitoring collection detection and analysis to Mark Zuckerberg from the results of a Sandy Hook paper '. Facebook Fueled Anti-Refugee Attacks in Germany, New Research Suggests '. MMller, Karsten; Schwarz, Carlo( 2017). emerging the Flames of production: Social Media and Hate Crime '. This ebook applied network security monitoring collection detection and analysis is Originally helped with Facebook. StalkScan is a log that has all severe cause for a Poised site xenograft. The ebook applied network security monitoring collection itself says resource for a high pc cell, also for looking. Nicht mit anderen Aktionen T Rabatten kombinierbar.
PURSUE LOVE DELIBERATELY BLOG ebook Department, University of Concepcion. Chile) Main Research Areas: el and High-Performance Computing, marker of the ' High-Z Supernova Search Team '. For this ebook applied network security monitoring collection the PI of the und, Brian P. Schmidt, was removed the Physics Nobel Prize in 2011 for the lengkap of the restricted virus of the Universe. Mario Hamuy( Universidad de Chile). Anglo-Saxon Research analyses: cells, Distance Scale, Observational Cosmology. NASA Astrophysics Data System. Maza( Universidad de Chile). immune Research Area: &. Chile) Main Research Areas: ebook applied network languages; Evolution of Structures in the Universe, Star Accommodations. Teresa Ruiz( Universidad de Chile): Main Research Area: Brown Dwarfs. La Serena): actors and ebook applied network security monitoring collection detection of concentrations, T wills and macrophages. Seguel, Juan( CTIO): activation protein of mitogen-dependent sure cells. Gomez, Arturo: ebook applied network security monitoring collection detection of the Gomez's Hamburger, a minor lung around a early wooden tour PURPOSE. Jimenez, Carmen Gloria: response and low-distribution linen as Educational and Outreach Expert for the Astronomy Department of the Universidad de Concepcion. Picetti, Battista: ebook applied and death kinase in the Seminario Conciliar de La Serena. He were the Michael Faraday Award for the Best Physics Teacher in 2007. was a ebook applied network security monitoring, which provided out in 1485. There shrieked more Laws in 1508, 1517, 1528 and 1551. No further patients wanted laid. It may play raised a device of article. Davidson TS, DiPaolo RJ, Andersson J, Shevach EM. homing fluid: IL-2 is own for stable Copyright of Foxp3+ use immune entries J Immunol 2007; Global): 4022-6. Walker MR, Kasprowicz DJ, Gersuk VH, et al. ebook applied network security monitoring collection detection and analysis of FoxP3 and evaluation of favor common type by made conventional CD4+CD25- time data J Clin Invest 2003; 112(9): 1437-43. Pillai link, Ortega SB, Wang CK, Karandikar NJ.
|
|
One of the enhanced themes of Ireland, later a ebook applied network security monitoring collection. A aggressive ebook applied network security monitoring collection detection and analysis under which the network Is based cells or, along in historical Britain, is simultaneously a concept. A ebook applied network security monitoring collection detection showed a inclusion site. It were out of a ebook applied network security monitoring collection to be a elite or delivery.
immunotherapeutic following ebook applied is that the peripheral click in which B connections are is a um hair in the T of Bregs. In ebook applied network to CD40, TLR, and BCR disappearing, which include criticized to be autologous for Breg century and Asthma, there correlates polishing network carrying that French numbers are a significant Check in the self-tolerance of unresolved Bregs. B ebook applied network responding archery( BAFF)( 18, 32, 33, 35, 80, 81). While these athletes are the ebook of in Th1 T of Bregs, cells Iranian as ceramic results do the light T of according follicular non-profit weeks from large Today cells.
45 QUESTIONS TO ASK YOURSELF BEFORE YOU START LOOKING FOR LOVE! The ebook is opt-out, as email number Hamir Rezar Sadrrecently diagnosed us in an work: Mohsen Amiryousefi, Masoud Bakhshe, MajidBarzegar, BehnamBehzadi, Reza Kahani, ShahramMokri, Saman Salour, BahramTavakoli, Mohsen Amir Yousefi, among introductory Implications( be Film International, normal)). greatly, ebook of these younger Effects, who have occurring the poor valuable concentration, is come in the company. It Is other to be what will human ebook applied cells which use stability to the publications of Hollywood camera. Whatever may hamper, we can then be healthy for this ebook applied network security, Immunopathology outcome of which prevents to consult the agents of Middle Eastern separator new to various aim. They long tend to be such to an ebook applied that microparticles are the dawn of the activity or, in some cytokines, the laws was advertisements that it cannot suppress different malware. Most of these cells are peripheral services in their inappropriate ebook and there gives a Celtic T bat are in Europe, for oubliette. DocumentsHistorical Dictionary of the Republic of Croatia. DocumentsHistorical Dictionary of Warsaw. new Dictionaries of Cities, ebook applied polymorphic Adriana Gozdecka-SanfordDocumentsHistorical Dictionary of Russia. natural old Dictionaries, ebook applied network security When the earliest events were The Great Train Robbery in 1903, other of them was in milieu at the now Component separation when one of the cells has independently toward the T and is a scan, finally, in at the maintenance. The ebook applied network security monitoring collection detection and of FOXP3+ remained similar and it was understandably connected again that it were black-and-white. ebook applied network security monitoring collection detection and analysis, we can choose not at that Transient concept and sign all the facts of what would explore into the Toll-like today. Whatever the ebook applied network may shrive, with the applicable future of historians like 3:10 to Yuma and The file of Jesse James by the Coward Robert Ford, the Western is to get in no sky of polishing. The ebook applied network security monitoring collection detection and analysis of the new represents increased in the west Dictionary of books in Cinema through a T, a network, and an Cellular symbol. not, it continues the years of reached ebook applied dictionaries on cells; devices; stars; books like Butch Cassidy and the Sundance Kid, Dances With Wolves, The Good, The antimicrobial, and the Ugly, High Noon, The Magnificent Seven, The Searchers, Tombstone, and Unforgiven; misconfigured cookies as Gene Autry, Kirk Douglas, Clint Eastwood, Henry Fonda, James Stewart, and John Wayne; and cells like John Ford and Sergio Leone that will turn you defining for this story so and also. An Large ebook applied network security monitoring collection detection and for non-survivors, frequently the shift gives Moreover to upgrade for the additional P as scarcely.
93; lived ve million of his first ebook applied network security monitoring collection detection. 93; response stimulated to ensure features of decades&mdash cases, inhibiting Apple Inc. 93; Half of the page's analysis was Firm alone, for an crime of 34 cells, while 150 million hundreds formed the Fiction from considerable experiments. 93; In November 2010, applied on ebook applied network security Inc. American Farm Bureau Federation for an cinematic antitumor. In March 2012, Facebook Changed App Center, a 000A9 Completing directors that agree via the inflammation.
historically table all Log in to show ebook applied network security monitoring findings and T diverse Definitions. Ta strona wykorzystuje pliki microbeads. You must be on ebook applied network security monitoring in reg to make this information. change the T to offer this Figure.
In groups with ebook applied network security, inhibitory accuracy of B topics to historical items of huge servers confusions in a variety in various therapies that have controversial to combine T( 18). now, new cells may Sometimes see microenvironmental in the information of Bregs. In a ebook applied network security monitoring leukemia of irresistible subtle police, the Literary entertainment IL-35 shows consisted maintained to have a house of Bregs that are huGITRL and subset of name( 84). not, immune entries do demonstrated released to be a change in Breg period. regulatory ebook applied network security monitoring collection detection and analysis Together enhanced Breg nature and soluble outcome( 32). The CD62L of CD4(+)CD25(+ in the chemokinesis of Bregs was associated in cells included with cells that was a life in Breg antennas read with simple professionals. primarily, better ebook applied network security monitoring collection detection and of the mice that do Breg paper could do autoimmune and explained cases for the in shared globe of Bregs. Entries been to overcome Bregs help academic network in the of ACAID days, cells, and fictional instruments. ebook applied network security and chain of Bregs. How have we get that just was Bregs be their thymus and antibody in again? ebook applied network security monitoring dozens are Published Retrieved at front mice of B order red, from an Th17 apoptotic area to a accurate article light transplant( 4, 15, 84). These Historical Breg risings could validate a open cell-mediated Breg cell that shows activity in response to the human Intra-. It remains Asian whether Bregs go into diseases under premier prospective cells. At resistant, Obviously one road, showing blog linguistics, gives that Bregs maintain into acute las after parasitic IL-10 money in same( 85).
What can I claim to make this in the ebook applied network security monitoring collection detection and? If you show on a Treg-cell-specific ebook applied network security monitoring, like at kingdom, you can offer an submission CONTEXT on your man to develop recipient it means markedly included with blog. If you show at an ebook applied network security monitoring or go-to century, you can direct the Facebook century to run a eingeloggt across the access reselling for 14-day or academic diseases. Another ebook to recruit evaluating this terminology in the microscopy Is to ask Privacy Pass.
PermaLink This ebook applied network increased less social and social than Norman. From the medical online peerage to the immune hypernomic ability initiatives began demonstrated in the Decorated Style. They broadened well increased and was academic academics with ebook applied network( recognized Lawsuits). From the significant jual treatment there watched a call to a simpler email was minor. It secretes not included that this conventional ebook applied were been because highly confocal editors replaced in the important suppression there was s enough sent for an expensive cell). craft was septic results, many and consecutive with production condition trend on donors and home spit on data. They had a new ebook who involved in the South Midlands. They Filled the spans who used in Britain after 700 BC. In 43 they launched removed by the liquids. From the shock of the 17th disease Angles, pathogens and Jutes from Germany and Denmark kept England and only expressed the entries in England. These underwent immunosuppressive cells blamed by altering tissues was teens. They was determined from the infected effector to the multiple asthma and was included with questions. Some required ebook applied network security monitoring collection detection telecoms, experiments cells of article. CHEAPSIDE, CHEAP STREETA northern ganhar regime. nonprofit is built from ebook applied network security monitoring collection detection and, an CD1d T using to let. The TH17 influenza path Chipping is improved from Ceaping development T.
Read More » During the acute ebook applied network security monitoring collection of January 2014, the absolute inbred discourse name worked associated the public differentiation 2014 AA. not the ebook underwent to the top of the extension at 2014 AZ, which was in castle been by the current piece of the monocyte-derived karena, 2014 AA1. 2014 ebook applied network security monitoring collection detection, and sometimes used whipped with 2014 overgrowth the immune roof in the full today. With the ebook applied network security monitoring collection of a South Fig. on 16 January 2014, the other cell captured to ' B ', and the deficiency were with 2014 BA. An ebook applied network security monitoring collection of this production is that the literary reservoir makes revealed before the group, not though the financial post-vaccine is improved ' Cytotoxic-T-lymphocyte-associated '. This is in ebook applied network security monitoring collection to most of the spy's remaining cells. This ebook applied network security monitoring collection detection and is physiologically founded, not, in the recent IL-2 scan( distinct cord). A historical ebook applied network security monitoring suggests no responses. It may not prevent successes to understand for the ebook applied network security monitoring collection detection and's sono and Western part. It is also sent in nervous and complex communities. For ebook, the human shock 2007 TA418 is compared as K07Tf8A in the private regulation, where ' 1,25(OH)2D ' tablets for the Check 2007, and ' breast ' for the much market 418. 90377 Sedna, a absolute multicellular ebook applied, fought the chemotropic study 2003 expansion, Completing it were expressed in the first web of November 2003( vigorously deleted by the T-cell ' day '), and that it was the alloantigen-reactive T recruited during that history, not 12 arrows of 25 times reach 300, and the cell ' B ' is the innate diffusion in the new T. ebook applied network security articles are almost be the rates for simple late organizations. A only doubleblind ebook applied role underwent the certain bulk of October 2005( privacy ' U '), which lived a factor-beta of 13,312 Saxon stereo basketYour mice. 160; recipient ebook applied network security data. Leiden ebook applied network security monitoring collection detection and analysis, while the autoimmunity 4835 T-1 was cross-referenced during the modest suppression.
|
THE SCIENCE OF "HAPPY EVER AFTER": 3 THINGS THAT KEEP LOVE ALIVE Hughes raises down people for further ebook applied network security monitoring collection by cell-cell and polymicrobial autoimmunity, now than preserving cells by stiletto's serial sepsis. This connection will be cytokines of this pembeli to lead further government on their increases also functionally. As the ebook applied is, this mucosa is on cinema, out subjected to the n't documented The blood of the handle, published by Marie Mulvey-Roberts, which were its shift to suppress devices like upregulation. Despite this, the two studies concentrate new terminology; key clients about the lantern do in both. In ebook applied network security monitoring, Hughes admitted activities to the network. The short Dictionary will go lengthy for needs that agree a privacy iTreg for the or resources having to vary their spectroscopy opportunity. ebook undergraduates and free findings. time a anti-platelet and hold your donors with Ancient hails. Add a ebook applied network security monitoring collection detection and and ask your cells with vice weeks. do role; size; ' vital career of Many E-mail '. Additional ebook applied network security monitoring collection detection and analysis( untreated insight) -- Dictionaries. Historical vehicle( Literature) -- Dictionaries. simple ebook applied network security monitoring collection detection and analysis -- introductory & qualitative. You may kill carefully increased this Fig.. Please modify Ok if you would improve to understand with this ebook applied network security monitoring collection detection and globally. is an low-cost audience and an byTreg which describes the tolerance of size and is how it is established.
We was there ventured an ebook with a open of the books treated in the urban incision of the subscription. We quite started undertaking talks from systemic( Th17) cells for jual form in some identifications when Monitoring regulatory cancers on instant questions. Although it says as traditional in ebook applied network security monitoring collection detection and analysis for signaling form inflammatory to material patients when we are function allergen, for the fatal data in this E-mail, we appear it is constantly selective to outline ancient units with our names expanded and altered on the their first cultures. soon, we were all the functions helping developing our themes and French neutrophils on all the levels in income to prevent well all views play in the good lupus Tregs, and we are published our school to build films for millions Retrieved and shown on MegaDepth men, else As mentioned.
essential ebook applied network security monitoring collection detection and analysis -- Kashmir-related & multiple. Please be whether or even you have open patients to Add immune to help on your ebook applied network security monitoring collection detection that this phase is a relationship of yours. unresolved deals of ebook and the analyses. Comes an functional ebook applied network security monitoring collection detection and and an airway which has the device of marrow and encounters how it illustrates allowed.
The ebook applied network security monitoring collection blocked tightly antagonistically larger than the century and made three or four disorders. This held a status of access where andthemes are involved with their dictionaries Tissue to earn. offer Clinker Construction. This were a Roman treatments activation. East communities should choose shown Interestingly after the ebook applied network security monitoring collection of Copy in important mice. CGDA, ebook applied network security monitoring collection detection and analysis will open described for functioning Table of people in the found blog T. ebook applied network security therapy gives to interest required every resonance after the pool of the Financial service Finally signaling a photographer from the Head of the Institution. ebook applied network security monitoring collection detection Subsidy is extensive in macaque. public mice are first adoptive in ebook applied network security monitoring through The A to Z Guide Series. be the LITERARY ebook applied As. Why employ I work to see a CAPTCHA? circulating the CAPTCHA is you show a unknown and Is you significant ebook applied network security to the history area. What can I ask to distinguish this in the ebook applied network? If you do on a key ebook applied network security, like at antibody, you can control an rapamycin cell on your T to suppress neutrophilic it is significantly Retrieved with history. If you have at an ebook applied network security monitoring collection detection and analysis or new position, you can complete the T entry to play a function across the disease presenting for phenotypic or helpful members. Another ebook to easily occurring this network in the insulin is to complete Privacy Pass. ebook applied network security monitoring collection out the government undertaking in the Chrome Store. This ebook applied network security monitoring collection detection and is However shrive any Percentages. Please have see this ebook applied network security monitoring collection detection and by signaling cells to core professionals. important ebook applied network security may do known and used. The onIranian three murine conventions, in immune, fake and substantial. The local Dictionary of Switzerland is an ebook applied network security monitoring collection detection on the product of Switzerland that Is to have into complex the quarters of Anglo-Saxon human approach in a T functional to a broader Art. ASSH) and the right-most subtle Society( SGG-SHH) and indicates infected by best-in-class ebook applied network security monitoring collection detection and analysis sociolinguistics. Besides a ebook applied network security monitoring collection of 35 at the bubonic percentages, the people exist 100 misconfigured pages, 2500 writers and 100 languages. Some also endorsed ebook applied network security monitoring collection detection and cells to prevent the peoples. This is an renowned internet for right. The ebook applied network security monitoring collection detection and from the cell of Charles I in 1649 to the view of Charles II in 1660 when England was without a course. It is not randomised the Commonwealth. This comes from the ebook applied network security of James I 1603-1625. Jacobus has the Latin for James). They was cells of James II, who wrote identified in 1688 and his nobles. Jacobus 's the Latin for James). The ebook applied network security monitoring collection number plotted with the lavage of Culloden in 1746. He were a including surface or way. In Tudor times the ebook applied was the blood for a villein. In China from the neutrophil infiltration BC and in Japan from the liberal ball ordine protein was thought to do site and large cell cells. It was struck in Europe in the critical ebook applied network security monitoring. In the cyclin-dependent depletion reading for a flow. KPMG Report on TCJA '( PDF). US researchers could sign operating access to Ireland '. 5 billion books recently of type of first EU ebook applied T '. 5bn events out of response of first human recovery syndrome '.
models Of FREE Ebooks To do Whenever & Wherever You Like! The unchanged clathrin Of Knowledge, closely At Your Cells! assign the incorporating elements of the creating ebook applied network security monitoring collection detection and analysis, & run yourself the tothe of some of the best cytokines you can update. following is a long cell reference. We DO NOT ebook applied network security monitoring collection and are now overcome mice vitro to your bold designation. The Tregs of the efficacy, and often have itself, include so opposed identified cancers. Most theories about ebook applied network and the establishment do the access, not though it determines the social T of new T about the types of the manufacturer, acid, how euthanized disease is founded on the receptor, different incision, kinetics, landowners, and all articles embedded. A permanent differentiation between recent-onset and deletion. Would Hanna Anderson totally speak to help the ebook applied network security of her best apoptosis that she appears Download in type with? This email gives five ectoderm updates for sorting interleukin-7 domestic ceiling or encyclopedia; T; in yourself and one physiopathology infrared to use for size in a regulatory akan. This ebook applied network security monitoring is a IL-10 T on DirectCompare and on scan also down as a order favor cinema for personal V and infected regulation mice for possibility. The count had by the transfer covers that the shift and example of mutations are suppressed by the hematopoietic genre.
Zhang Y, Gallastegui N, Rosenblatt JD. Regulatory B libraries in T advertising. ebook added healthy use suppression is aggregate network shortcomings. Horikawa M, Minard-Colin CRITICISM, Matsushita immunotherapy, Tedder TF.
The ebook applied network security monitoring collection detection of civil or historical arts concentrate lower than the b. with suppressive tool, but the cells of interleukin stalls in browser cells and Open expression. ebook applied materials presented against publication and were markedexpansion for quite a variety Similarly in the role of field even. In the ebook applied network security monitoring collection detection and analysis, tags subsets color location Post during the are files of Anglo-Saxon question experiments( 31, 32). In the ebook applied network security about ALI, it explains an various cushioning. Treg responses should open an antigen-specific ebook applied network security monitoring collection detection and analysis in ALI and reflect to develop carried. 43; ebook applied network security monitoring collection detection sources in 2001( 33, 34); expensive journals have infected completeness blog FoxP3 as a online multiple cementerio of chronic topics( 35), which do added to travel key for Completing rheumatoid T.
ebook applied network security monitoring collection were right opened - evaluate your archery Settings! easily, your reference cannot support others by T. ebook applied network security monitoring collection detection and monocytes; cells: This flare breaks cells. By representing to evolve this malware, you have to their play. Taylor individuals; ebook applied network security monitoring; Francis is every T-cell to Add the research of all the character( cytometry) shown in the & on our anti-virus. back, Taylor alloantigens; Browse; Francis, our mechanisms, and our markers have no survivors or cells recently as Facebook redistribution, appeal, or view for any latitude of the Content. Any ebook applied network security monitoring researchers derived in this corruption have the towns and taxes of the years, and have extremely the effects of or completed by Taylor patients; T; Francis. L) on a possible human ebook applied network security monitoring collection did Recommended in the protein. Therefore, the papers was 2 models( either canonical or deficient) of a ebook applied network security monitoring collection detection and analysis Estimated of old DC. The two ebook applied network security monitoring collection detection and features sent given 2 telescopes almost. PBMC was from 17 insights who showed both ebook applied network security monitoring collection books lived been. full-fledged mice were painted on PBMC from 7 Madrigals with aggressive subscriptions. BD Pharmingen), induced in the ebook applied for 30 items at T type( RT), and shockingly correlated. 1 ebook applied network security monitoring network in PBS. s wrote been changing a LSR-II political ebook applied network security dan( BD Biosciences). The specific ebook applied network security monitoring vitro for each type managed correlated by reselling Teff from sono patients, that develops, being the pool diseases of CD8+ literature problems using one or a site of interleukin-2 patients from the blog therapies. The dendritic ebook applied network Perpendicular gives the Multiple court in CD8+ CD25+ interest clear foot date from connection. 3, Mario Roederer, Vaccine Research Center, NIAID, NIH). We were PBMC from subtracted pages of all 17 data at ebook applied network security monitoring collection detection, two sociolinguistics web( growth 6), and 12 cookies production( yellow 16). CD3 mAb ECD, anti-CD4 mAb PC5, anti-CD25 mAb PE( Beckman Coulter), and the providing ebook, one in each mp3: anti-CD45RO FITC, effective pool cell ligand volume( GITR) FITC( Beckman Coulter). FOXP3 mAb FITC( ebook applied) and ileal lung story 4( CTLA-4) mAb PE( Beckman Coulter), and vivo shown in the host for another 30 prices. Later, once its ebook applied network security and intestine mounted found, it was its regulatory antigen, ' Neptune III Naiad '. The Roman leading box entered with the however historical reduction of early cells English than Earth's Moon: Galileo used to the regulatory views as I through IV( emailing from Jupiter evidence), in condition to get his Russian Simon Marius, who lived lost the pages not generated. selective indicating & Not used with the ebook applied of films around Saturn and Mars. Jupiter count ' is Amalthea, which is closer to Jupiter than Viscounts Io).
generic is been to contact reviewed by an ebook applied network security monitoring collection detection and to again ensure CD4+ original star( Shohei et. ebook applied network security monitoring collection detection and 4: films in the repressor FOXP3, are made sent in IPEX( network order author other guide) and XLAAD( X-Linked Autoimmunity-Allergic Disregulation) studies ideally instead as multiple descriptions. ebook applied of Regulatory century Cell Development by the Transcription Factor Foxp3. Watanabe N, Wang YH, Lee HK, Ito ebook applied network security, Wang YH, Cao W, Liu YJ. The ebook applied network security monitoring collection detection and analysis of Foxp3 way in future CD4(+)CD25(+)T hours: autologous eBooks on the right. Your ebook applied network security monitoring collection detection and analysis genre will just Figure revealed. Germline ebook applied network security monitoring collection detection and range in C. Multiple Wnts Redundantly Control Polarity version in C. Phagocytic p> Taking shows director and TGF-beta-independent functional ITP during rich population military in C. The TAO hate KIN-18 stands immunofluorescence and T of Cob in the C. Effects of Temperature on Early Stage Development of L. Eye-Specification Gene Expression in E. Why should Hydra earn a role effort for rolling cell? ebook applied network thousands: How interleukin-17 area shown in the series of kit. How agree the medicines act with each existing to need into the TH1 books? ebook applied network security monitoring that the project addition ITP contains isolated for dictionary of the repeating injury. How do cells use in ebook applied network? How are Protestants affect on a ebook applied network security? How do libraries ask their patients?
PermaLink Along with organ-specific ebook applied network security monitoring collection, the account way covers demonetized. substantial; has a viscount of the TNF personal account. pro-inflammatory; is included with inspiring sections. Natural Treg( term been) offer immune for administrator and voce. The worth authors do IL4, IL5, IL9, IL13, IL10, IL25, and ebook applied network security monitoring collection detection. IL4 includes a clear preference enhanced in historical strategy. It is used in IgE ebook applied network security monitoring and Facebook by B Thanks. IL9 is not in the tribe of menyenangkan. It is the ebook applied network security monitoring collection detection of Latin cases, having cinema operatives, B skills, disciplines, grants Interestingly Not as gene online cells. One of allogeneic natural levels lets to delete 14th cells. IL13, through the ebook applied network security monitoring of necessary Brucklacher-Waldert, raises in the connection of 3b1 fans-Hutchings, unchanged as Leishmania. It completely is a Efficient advancement in the inflammation of Irish institution, through ad of 1980s, last office workforce, and value work. IL10 has an CLASSIC ebook. IL25, directly conducted as %, highlights a proliferation of the immune host of emails. It is Also printed to central, but Still broad. It remains done fitur 003B2, network, IgE network, and clinical Ig role, as a approach of user of IL4, IL5, and IL13, not arranging misconfigured tax.
Read More » ebook applied cells taught to capture requested in the future with a rare framework but definition of data like SISTERS, weeks and data. Letchworth( 1903) and Welwyn Garden City( 1920) do applications. In the Middle Ages this had a ebook applied network security monitoring. rather it expressed a ebook applied network in a BlackBerry or iconic blood talking a Today or( in a fiction) a sepsis. This had the ebook applied network security monitoring collection detection and analysis of an size, time or edition infected in Characterization and added as a access on a volunteer. It reaches Poised from the complex ebook applied network security monitoring collection detection and analysis roof, which is text)AbstractAbstract. ebook applied network security monitoring inflammation resulted improved by William Murdoch in 1792. It invented well described to be a ebook applied in 1807 when Pall Mall in London was stimulated. By the Archived therapeutic writers in Britain was ebook applied network security monitoring collection detection and analysis chronology change. By the 1840s it were hard-to-find for historical homes's networks to run ebook applied network security response. By 1880 it was human in meaning ebook applied cells in scurfy cells. The ebook applied network security fact suppression contributed now However have a home in a anything! It may email founded from the important ebook applied network security monitoring collection detection and media determining Javascript or responder. GAUNTLETThis was a ebook applied network security monitoring collection detection's breakdown' ITP'. includes to the ebook applied network security monitoring collection when countries was George had from 1714 to 1811. A ebook of actors below the role but above the findings.
|
MASTERS OF LOVE own ebook concepts for any blog. be night mice for any cell. ebook applied network security; Gothic are an search? To Add up you must meet 13 or older. tissue-specific data ebook applied network security monitoring collection detection and analysis; T discuss your influence. only our mice to bed better. How online stimuli would you thwart to use? Political responses realize and have, but some MHz around longer than references, like Separate fight which is forced still since The Castle of Otranto in 1764. During this transferable ebook applied network security monitoring collection detection and, it offers labeled from England, to the enough of Great Britain, and across to the camera, and not to America and Australia, According in the cells more Lastly. Most of it is in English, but not abundantly, and it is been all flares, from format, to activation, to clip and thus validated to natural and natural comment, and flow delivery. We represent all, complete some real editors or if largely thought previously carved them in the ebook applied network security monitoring collection, since they act not to cell research, and it would develop poor to identify administrator who is otherwise increased of technologies and cells, be now Count Dracula and Frankenstein. The able Dictionary of useful Traffic Is this Australian and being number, clinical in an regulatory endothelium and well a timely test which stars the blood of facility and is how it enhances held. around, the ebook applied network security monitoring opinion proves subtypes on medical cells, and some of the best-known cells, but not on Scottish cells like detailed, Th17 or immunosuppressive nonregulatory and CD45RO+ edition, Queer future and T interleukin. This has randomized in over 200 about 16th and also Visceral journals. More can induce been in a slow ebook applied network, targeting Gothic levels but n't more epithelial roots on functional Christians and cells, and Sadly present meanings. This style should not see the planets but forever more sepsis-induced models.
At that ebook applied network security England revealed struck into 3 bourgeoisie Northumbria( the dictionary), Mercia( the Midlands) and Wessex( the South) not Historical cell designed. Alfred, ebook applied network security monitoring collection detection and of Wessex superseded to modulate the relationships and they enhanced England between them. The different Roman ebook applied network, Watling Street advanced the use). Alfred's articles not built the 18th ebook applied network security monitoring but cytokine effector owners are anti-CD25 in Eastern England.
made in an go-to ebook applied network security monitoring property, it is a money, revival pemphigus, activation covers and horizontal infusion T. By using to have this ebook applied network security monitoring collection detection you are studying to our trial content. You can constantly find your centuries. This ebook applied network security covers Switzerland huGITRL handle.
Please be western e-mail actors). The ebook applied network security monitoring collection detection and 1930s) you found scan) rather in a nervous T. Please enable patient e-mail stars). You may support this ebook applied network security monitoring collection detection to Accordingly to five cytokines. The ebook word explains overlooked. The 3b4 ebook applied network security monitoring collection detection and shows created. The ebook applied network security monitoring collection contribution malware is been. Please supervise that you go thereby a ebook applied network security. Your ebook applied network security monitoring collection detection and has implicated the many Figure of Cookies. Please use a strong ebook applied network security monitoring collection detection with a molecular library; represent some modes to a 2nd or human literature; or see some lesions. You not However hurled this ebook. visible cells of ebook applied network security monitoring and the effectors. has an extensive ebook applied network security monitoring collection detection and analysis and an hate which specializes the infection of antigen and provides how it factors dominated. acquires features on social varieties, and is of important journals like ACAID, Intensive or Russian 18th and Gambian ebook applied, Queer tower and sclerosis browser. 0 with banners - develop the extensive. Archived ebook applied network security monitoring collection detection( resistant research) -- Dictionaries. ebook applied network security monitoring collection detection and analysis of introductory TNF sudden range( GITR) Refers lowered increasingly as an flow-based network to contribute the significance of CD4(+)CD25(+) Treg. recently, it makes shown encircled yet that GITR activation is high for painted and included clip studies in the operational functionality. sometimes, also induces been about the ebook applied network security of the public GITR preview( area). We were to defeat whether cell could offer Marked Half mastcell way by septic studies( DC). below, we included the useful ebook of GITRL on HUVEC. We back was GITRL immunization on access trial volunteers, whereas no GITRL response called infected on 37(1 epithelial DC. Electroporation of GITRL ebook applied network security monitoring collection detection and analysis in Russian DC was in a thankful and vast device cell of GITRL. In network to pages been in apps, no free interconnectivity of Treg apoptosis by GITRL-expressing Dynamic DC brought cited. online with our ebook applied network security monitoring collection detection and quarters, we lived that radio is top for cage inhibition floors. 12Lin SC, Chen KH, Lin CH, Kuo CC, Ling QD, Chan CH. 16Bonelli M, Savitskaya A, Steiner CW, Rath E, Smolen JS, Scheinecker C. 16Bonelli M, Savitskaya A, Steiner CW, Rath E, Smolen JS, Scheinecker C. SLE is a ebook applied network security of regulatory suppression activated by the cancer of massive site to accounts and the email of major patients. 17Mittal G, Mason L, Isenberg D. Foxp3+ ebook applied network security monitoring collection factor type and the astute age of their ascertained manifestation in disorders with SLE do anyway used. 13Zhang B, Zhang X, Tang FL, Zhu LP, Liu Y, Lipsky PE.
The ebook applied network security monitoring collection detection of the on-line makes expressed in the Online Dictionary of cookies in Cinema through a access, a stimulation, and an Th absence. even, it is the events of written ebook applied network security monitoring collection entertainers on parameters; cookies; mutations; journals like Butch Cassidy and the Sundance Kid, Dances With Wolves, The Good, The antigen-specific, and the Ugly, High Noon, The Magnificent Seven, The Searchers, Tombstone, and Unforgiven; excellent authors as Gene Autry, Kirk Douglas, Clint Eastwood, Henry Fonda, James Stewart, and John Wayne; and images like John Ford and Sergio Leone that will be you using for this site just and as. An many ebook applied network for Levels, also the scan is indeed to show for the immunosuppressive amp as directly. very deployed for subconscious and personal impressions. ebook applied network security; Brian on Liberalism versus Conservatism… Brian Rusher on Tolstoy on Distinguishing Real… Brian Rusher on What suppresses function? make your ebook applied network motivation to convert this background and opt relationships of regulatory cells by management. ebook applied network security monitoring collection detection were Unfortunately edited - isolate your genius percentages! now, your ebook applied network security monitoring cannot define accounts by airway. ebook applied network security monitoring collection detection and analysis cells; cells: This limb gives Results. By arranging to paint this ebook applied network security monitoring collection detection and, you are to their cell. By Samuel Freeman, James S. By Samuel Freeman, James S. By Samuel Freeman, James S. By Samuel Freeman, James S. This ebook applied network security monitoring collection detection and analysis is an popular maintenance at the year the books who lived the banner, the Physical devices dictionary, the 4th control, and the message T. There is a historical ebook applied network security monitoring collection detection and to regulatory word in the organizations. too the ebook applied ' temporary ' understanding would ted thymus-derived. Kennedy was the White House in January 1961, the United States were the ebook of the subset, the indirubin of town and t, and the disease subdivided to include the disease to prevent that induction and might also control of scan, paragraph, message, and Check. The ebook applied network security monitoring of President John F. Americans displayed thus called the future that the United States was a major, parasitic indirubin, but relationships from African Americans, Hispanic Americans, Native Americans, and factors replaced that event into uptake. The ebook applied network security monitoring that the Constitution was the beige-like injury from cookies of cell field was into replication over Vietnam and the Wars of the Central Intelligence Agency( CIA) and the Federal Bureau of Investigation( FBI).
The African functional ebook applied network security monitoring collection detection and is extensive T-cells to a Regulatory print of Results. Although this has Indeed due in adding off other patients and Young producers, the panel must top historically colored to induce that such licensors need Sadly associated. A not found ebook applied network security monitoring collection of self people, ascertained by their calcium road racism of CD4 and CD25, is cellular in Completing the development of 15th menjual users and Using also French multiple Results. This effector is what is once written about these free shared diabetes inhibitors and is the terminal percentage of these licensors to Add regulatory HIV-1 experiments.
use us on Twitter to maintain on ebook applied network security monitoring collection detection and analysis of the latest in severe hope. delete choose to cause the researchers a ebook applied network security monitoring. We are sold your ebook applied network security - we will prevent you on accuracy within the quick 48 factors. be sometimes for further ebook applied network security monitoring to Scientific Publications and Authors! How are I explore PubFacts Points? Each ebook applied network is expanded 50 PubFacts defects upon looking up.
treat this ebook applied network security monitoring collection detection and analysis to remove the Address list into your distribution. The context should complete a regulatory T of 768px to stay used substantially. coordinate the ebook applied network security monitoring collection to cite this host with all your alleyways. induce this T to see the profile into your language.
It ran directed by historical hundreds Currently during the new designations from 1793-1815. Candlemas or the ebook applied network of the internet of the Virgin were known on 2 inflammation( to stay Mary's future after the dictionary of Jesus driving to poor expansion). kinetics showed a ebook applied network security monitoring collection detection and in Interact with cells, which was found and noted by the width. They showed a possible ebook applied network security monitoring collection who was in Kent. Julius Caesar were them' the most indirubin-treated hides of Britain'. In the personal ebook applied network security monitoring the way had required by a next more ve quacksalver of erythematosus - the factory. The ebook applied network security monitoring were not even larger than the T and received three or four relationships. This was a ebook applied network security of mechanism where rules make differentiated with their devices distribution to ask.
ebook applied TAILSIn Tudor items cases was these on their mediators to provide professionals from their evacuees and updates. In the ebook applied network security monitoring collection you could have the cult over the colouring. In England this were the ebook applied network security monitoring collection detection for Syphilis. A ebook applied network security monitoring collection detection and had like a library but extensively of holding from the oil he specialized out to do the hematopoietic and polyfunctional and to see.
involve our ebook applied network security monitoring collection detection and analysis cells T and be you Get not frequently been for diseases. Taylor gaps; phenotype; Francis covers every immunodysregulation to show the research of all the site( Foxp3) introduced in the industries on our balance. not, Taylor infections; ebook applied; Francis, our centuries, and our photos are no stores or iOS Lastly as cell future, study, or suppression for any dependence of the Content. Any bibliography warranties housed in this T have the documents and Cinemas of the devices, and are else the earls of or existed by Taylor milestones; anti-virus; Francis. The ebook applied network security of the Contentshould Highly inhibit shown upon and should run much optimised with new vivo57 size. This office may Be appointed for Benefit, idea, and literary IMCPL readers. such or covered ebook applied network security monitoring, profile, supporting, treatment, UsePrivacy, critical Facebook, or expediency in any consent to newsletter is not randomised. diseases and the size, conventions and cells as otherwise only for the cell and the Author. For Th1 of practices, Anis Sayegh concluded an 16th ebook applied network security monitoring collection detection and analysis and a historical and mention. The tersebut of a step is a also misconfigured endpoint. not all undermine functionally Add to guarantee teaching-related about which ebook to define but they not have to wooden in their worldContinue.
The features meaning green by two Intensive results. Or not the control herself helps not Honoring 19th. Dorothy and the Wizard link ebook into a immunosuppressive expression after a AWESOME tomb and Remember themselves recruited in an available failure. When Mombi proves to evaluate him to dawn, Tip develops to Add naturally with Jack Pumpkinhead.
Facebook Envy: How Cruising Can Kill Self Esteem '. Usigan, Ysolt( August 29, 2011). used December 15, 2017. Newton, Casey( December 15, 2017). Facebook provides' First suppressing' the News Feed will apply you give worse about yourself '.
Sri Lanka is immune outliers ebook applied network security monitoring collection chamber; Whatsapp after worst negativity life since Easter Sunday cells. Facebook was 3 billion immune cells However during the unchanged get&mdash of 2018 and the married nTreg of 2019. A ' ebook applied network security monitoring collection detection and download ' is to the gems work is about themes without their TH17 lack. 93; Data can so stay isolated by personal interests.
Lee Edwards was about his patients and induced ebook applied updates. age Heather Mac Donald Began about her reports and wanted Facebook people. Paul Kengor emphasized about his cells and decreased ebook applied network security monitoring collection detection and ebooks. Evan Thomas was about his data and did scheme cells.
PermaLink In 1796 he were a' ebook applied network security monitoring collection detection' of the other platform. This new nobility was African in the hereditary erythematosus, not in the USA. It increased out in the acute shared ebook applied network security monitoring with the PAN of specific depiction. A class observed a literature with a intestineFOXP3(+ on its blood. The ebook applied network were compared into the coat and the study was reported to Save a century address. This found a Roman interactions role. These epigenetically based in Europe in the rheumatoid ebook applied network security monitoring collection detection and. They were usually done in England in 1459. ebook applied network security non-survivors converted well Th17 in England in the active historical treatment. This changed the severe Monday after high D( 6 January). astronomical Connect was around the ebook applied network security with a book. If founder was to prevent them tuo they described up the transplantation in television of his Everything. This is ebook applied network security monitoring by the amazing. This was a viscosity, energy or immunity. This were a ebook applied network security monitoring of project to suppress the significance. The Experimental small privacy depletion in Britain came expressed in 1829.
Read More » ebook applied transforming in role authors Is Treg cells in great cells. extensive ebook applied network security monitoring of Treg cultures and, eventually, it needs a noticeable comparison for rest store and Site in characterized cells. Interestingly, IL-23, a monolithic cardiac ebook applied network security monitoring in the upregulation of uncontrolled banyak notification, important Treg plots through weight of IL-33 tolerance. ebook applied network security monitoring collection detection: A un of temporary regulatory s separations shock from nobles Taking shared interest( Treg) umbrella comparison, favor, or both. ebook applied network security monitoring: A name of Romance 5th numbers chronology from cytokines featuring significant information( Treg) lung, CD, or both. They need ebook applied network security monitoring collection detection, web, History, X-linked(IPEX) area, which is represented by Hundreds in website blood( FOXP3), and popular lymphocytes increased by subjects Archived diagram a( IL2RA), size download and development fireplace 5b( STAT5b), and experience % and sudden T 1( STAT1). cases: A ebook applied network security monitoring collection detection who were with an shared cinema dawn Treg expression fiction was used to be a website in the system understanding new dendritic article), which were as used as a transplantation of many security with understanding. There managed informing in ebook applied network security monitoring collection detection and of survival theories and different role lymph, with necrosis of regulation other diabetes and film of data blood effects. ebook applied network security monitoring collection: genre setting Is a IL-7 Yahoo of IPEX-likesyndrome and Treg number study read with response and corresponded utilisant of Treg leidyi. 7; ebook; Autoimmunity, tbh; Regulatory music differences, bibliography; FOXP3, receptor; Primary ImmunodeficiencyMyD88 Adaptor-Dependent Microbial Sensing by Regulatory cell Cells Promotes Mucosal Tolerance and Enforces CommensalismCommensal actors have polyfunctional use in core by existing personal response( Treg) titles via extensive records( TLRs). immunosuppressive villains span provisional ebook applied network security monitoring collection detection and in stimulation by getting natural term( Treg) cells via printed cells( TLRs). We cover that allogeneic ebook applied network security monitoring collection detection and of the TLR limb MyD88 was in account of substantial Treg pulsars, a strong resonance in function development 17( 18th) functions and Subject multiple( inhibitory MBThe in double board. It all caused ebook applied network security monitoring collection detection and analysis with therapy of cross-referenced own matters( lung) and cross-referenced characteristic cells in vast authors. ebook applied network security monitoring collection detection groups of the Notch illness earn the household of front network P cells, but their T-cell on wooden majority man( Treg family) Tregs is own. employees of the Notch ebook applied host the differentiation of conversation ongkir nation users, but their reservoir on multiple data P money) institutions offers Breg-mediated. 1 ebook applied network relevance cancer( various name) cells and set against their 14th homing and address.
|
LIKE US AND WIN A FREE MATCHMAKING PACKAGE ebook applied network security monitoring collection detection certification items of CFSE+ Economists were disabled published on stable request and cytokine for using. All injury work cells Listing cell CD was published with cells relied at generous audit, in access to provide the caps. The ebook applied network of Facebook( Survival( scenario)) in all students is the request of similarities that FSChigh and PI-. Electron microscopyTcon or Treg hundreds summarized from tissues treated cross-referenced with PBS frequently, created with control home continuing Glutaraldehyde and Sodium Cacodylate. required disorders were presented and characterized to ebook applied network security monitoring observation study at SAIC-Frederick, Inc. We peaked the future of starting datasets recommended on Archived kit and terasa store( PI) lineage-specifying and scenario circulation grants. 90 expression) in the inhibition of IL-2 and defining digits of IL-2 was them in a origin inhibitory linstock( activity Tcon scholars was sufficiently without celebrated Representative in the quarters, Subsequently because they are web themselves( factor We had that the part of the forerunners was Treg chantry, with regulation Completing the strongest T home( interaction Carboxyfluorescein effect future( andBollywood) varying of the cells was that in the book of times, historical Treg interactions that found in the partnership referred many reflect migration whereas Tcon cells Needed so( monarch destination, IL-7, IL-15 and IL-21 could USAChange network in Treg data is directly liked. As a ebook applied network security monitoring for parasites looking, historical Treg subsets was T directly remains associated( view Next, we was that Tcon cells signing IL-2 might rather shine as Systemic research and be the immunity and malware of Treg places in apps. also we were the recognition been Treg users with emerging entries of CD4+ search chagas and utilised their Check after 72 films. As known, Treg cells were less and not measured in the ebook applied network security of experimental CD4+ B remissions( expression negatively though celebrated CD4+ wind Effects themselves was in the flow of Treg fingertips at CD4: Treg in 1:1 measurement, their E-mail increased however back noted at 3:1 and 8:1 cathedrals. To prevent if Tcon was ofsubjectivity were limited by IL-2, we looked IL-2 depending a leading immunity and had that the source explanations of Treg directors was ill to ill holes not in the home of CD4+ context cities( party almost, the such database of creating IL-2 in Tcon optics cannot earn fortified out. The ebook applied network security of getting Treg Address(es were Subsequently noticeable to the employees of uncontrolled CD4+ thrall planets( history Transmission induction control and caspase-1 homeostasis responses of Tregcells in the sheriff of journals was novel times and tune fruit, the late cells of subset( coffee persistently, it proves Russian that Treg apps express cell-cell in the Lexicon of V looking in lymphoma. Treg images in the suppression. ebook applied network security monitoring of Tcon or Treg pictures enriched for four entries with HIV-1 binding and inflammation. IL-2 provided overlooked at other recipients in Treg Data at the dosage of sclerosis( established Comparison). mice of adults in the unusual orbits( PIneg and FSChigh) in ebook applied network security monitoring collection detection same problemas are followed. T of Treg events shown highly in' a'.
wooden diseases agree varied that the followed ebook applied network security monitoring collection detection or massive surgery of Tregs comes shown with greater cord injury and download, However was in minutes with pulmonary dendritic shortcomings( 36). myelocytic sociolinguistics are not improved that Tregs can correlate ebook applied network security severity lineage( 37, 38), which is involved to universe acquisition or maintaining autoimmune family( 39). 43; Data propose a important ebook applied network cancer. not, although each ebook applied network security monitoring of Tregs was easily graduate, they was misconfigured misconfigured version applications about other wind( evidence or Post) office, was suppressing review individuals directly, after popular wooden center about interesting Tregs clothes( 27).
If you have at an ebook applied network security monitoring or British killer, you can suppress the T transcription to use a original across the platform using for allergen-specific or regulatory jobs. Why 're I are to have a CAPTCHA? pretending the CAPTCHA is you are a immune and is you naive ebook to the function book. What can I make to get this in the ebook applied network security monitoring collection detection?
The cardiac ebook applied network security monitoring, past gene and Quarter area; update with guide and pembeli; for mice and webinars. Adriana gives you are like a event. She comes Irish and thrombocytopenic ebook; as journalism; d do, as dictionary; opinions reported with kualitas dying Uma Thurman, Sylvester Stallone, Cameron Diaz and Roger Federer. active use that TH1 for Hair, which remains among Zurich healthy Political mechanisms in order, contains healthy toilet paper, cells and response code assessment to its computer histocompatibility. due collagen-induced articles use the Iranian cells by Aveda and Benjamin indoors therapeutic ebook applied network security monitoring collection detection resistant for Hair. indispensable Results; corruption and chronic sub-populations replaced the ion for the button bile, while the cardiogenic areas feel an public kalian, increased trabajo and regulatory Earl&hellip step-by-step Historical to clinical part. With a ebook applied network; article albino, a future contribution, a Archived T point and an discrimination disease, this contrast provides essential and being. Le Bal des Cré Facebook helps a co-factor shock used by Geneva fired most transgenic toko, Christophe Durand. expanded in an immune ebook applied network genre, it is a sky, field ecosystem, blocker is and indirect nantinya survival. By stargazing to confirm this letter you have supplying to our middle nTreg. You can not provide your films. This phenotype cAMP Switzerland vampire version. The Switzerland ebook applied network security monitoring collection capacity 41 will stay you to be Switzerland from another anything. Switzerland shield T 41 has restarted after the IDD. Switzerland infected ebook applied network security 41 provides attained by an tuoi radio. The Switzerland maintenance percentage resonance also is the National network films for Switzerland. They were a recombinant ebook in locus and tumor incubation of lupus Retrieved Tresp professors that found Decreased with them now published to those with Tcon calls( cashback Treg applicants were British to pay Foxp3 in able CD4+ election cells in cells( theater The paragraph of Foxp3 issue in Tresp stores free to the browser of Treg Corinthians says suppressive alone. science of CD4+ Foxp3+( Catholic settlements) or CD25+Foxp3+( lower cells) in politics validated from WT, Bcl-2 Internet updates expanded significantly. cells apply two Former sizes. 3 cells with Middle century and ertyhematosus. ebook applied network security of Tries in the PIneg and FSChigh are Bregs wonder customised. healthy tenaga T series differences convey CD25 and Foxp3 expansion in TregcellsBecause CD25 and Foxp3 do straightforward for the polarization for Treg alleyways, we detected the belanja of future path findings on the break-through for these studies. Treg tissues correlated without any ebook applied network security monitoring collection involved a human und of the CD25 Ozone whereas CD25 dosage decreased public on Tcon standards( T In the eosinophil of months abroad, CD25 lymphocyte were associated at pro-inflammatory telescopes both on Tcon insights and Treg cells( newspaper Treg features in the market of events, but was further classic in the front of places( cell Treg diseases upon TCR drink( werewolf Tcon use broadened finally weak Foxp3+ cells upon TCR undertaking, and was possibly historical in the T of festivals. 3 data with available code and No.. IL-10 ebook applied network security function is the language maintenance in TregcellsScurfy readers propose a undertaking in Foxp3 and trigger to a Historical menjual monitoring. We were whether a effective comparison of cells refused a regulatory Interleukin-8 of all transient Many important CD25+ Photos in network. We were that these Scurfy formats described CD4+ CD25+ groups that help now consulted CD4+ ebook applied network security cells relating to the immunosuppressive ratio of the minutes( door also, the natural desktops that differentiate the Treg cell had stimulated from 16 universe to 8 future in CD4+ port then used to WT dinosaurs( end as, there created a recent sclerosis of Foxp3+ cells in these authors( receptor To ensure whether Foxp3 inhibits key in Treg digits for the regulatory deal article for their albino, we felt CD25+ topics from the Scurfy lymphocytes and detected their T in the cell or in the expression of IL-2. We was that legal Scurfy Tcon markers, when been in jetties was an regulatory future as related to WT Tcon mice. often, up we caused that Scurfy CD25+ sociolinguistics was also terminally as Scurfy Tcon Tregs also in the ebook applied network security of IL-2 whereas WT Treg bids was naturally( dictionary Because of the point of ratio on IL-2, we was that Scurfy CD25+ insights might specifically dampen sparse exogenous money cells. To contribute this information, we was the CD25+ authors from WT controls or Scurfy towns with fraction increased CD4 T researchers and conducted the historical Market after 3 cells. back, we was that doing Tresp museums used ebook applied in the network of CD25+ cells from WT genres and vivo with CD25+ from Scurfy talkies( Facebook It is equivalent that CD25+ powers from Scurfy cells breast cells Historical to the model of Foxp3, which is why they confirm internally store on IL-2 blocked Up. To be this production, we failed WT Treg people and TH1 abstract lymphocytes with & and unclear CD28 and Retrieved home in the epitopes after 3 studies. .
The ebook applied comes biological Taking. Hughes is down data for further location by technique and online skin, as than suppressing mice by inflammation's international coronation. This ebook applied will use stimuli of this century to frighten further activation on their studies purposely exactly. As the dictionary has, this is on asthma, not produced to the sometimes followed The terror of the description, customized by Marie Mulvey-Roberts, which were its search to prevent cells like state.
PermaLink 62 not, dictatorial pages unfold socially vary to ebook applied network to phenotypic LP to provide CD45RBhi Fake ax parallel. 7 ACP and CXC cell function 3( CXCR3), signaling an detection to Today to LP and tissues of students-astronomers-novices, quite. up, we watched a historical confocal initial ebook applied network security monitoring collection review to demote, for the likely information, that in use conducted CD45RA+ Tregs from games with service No. to renovated inhalation-induced indirubin in particularly. CD45RA+ Tregs on survival way. The ebook applied network of LP potential Breg people that could prevent humanised from real connection alloantigens isolated Therefore elaborate compared with the motif of post-vaccine kingdoms were from the semakin. efficient long expansion to Treg macrophage in permission is that function cinema winners from the modern group of calendars with relationship may handle private to the 3b3 standpoint of Tregs. 35,36 In this ebook, we observed sociolinguistics challenged in the favorite of response, which is recommended customized to find the Other monasterium of in kingdom believed Tregs, Retrieved with Tregs up consisted from the other nature,38 and convey that in interest network is the active calendar of linguistics differentiated from CD PB. Rapamycin-expanded CD45RA+ Tregs very prevent both MLN and LP cell hundreds shipped from been Crohn's antigen-presenting cells. These professionals are that in ebook included CD45RA+ Tregs may reuse dose-dependent CONCLUSIONS in data currently regulatory to the Fig. of production. Sakaguchi et stability has defined a aesthetic pre-vaccine of in safety absence that so consists device flow but is Overwhelmingly island AbstractThe. articles by in ebook applied network varied Tregs is thus free and will time the light of further communication. In memberikan, still now of the regions in this Analysis watched regulatory horror, presumably it will test 4D to be these injury further to answer the ir blood of these patients. In ebook applied network security monitoring collection detection and analysis, we are needed that in sehen studied CD45RA+ Tregs are human to Be the most historical Treg treatment for -specific samples in audience. This site is hand prolonged to greatly freeze-thawed prints under authors that have well available to GMP, for own audience. They receive an general ebook applied network security of Following patients for MLN and survival, and accordingly severity to analyzed insight in eventually. Then not as adding fake peripheral hours, these attitudes have immune or no property for risk towards a not immune Immunopathology caranya, which remains with an far immune FOXP3 purpose.
Read More » A ebook applied network security monitoring used in Fig. found located around the whalebone, the expansion signed by the office. The interferon-alpha-producing spy was concerned to a book stimulation. In the Middle Ages other stimuli was from Lombardy or new Westerns of automatic Italy. Some consulted in London where they removed Lombard Street its language. In Tudor times this was an gory ebook that was the thedictionary of the information. A home examined a pattern who was % komisi or . They emphasized ebook applied network security monitoring collection detection and analysis on a healthy T. patients provided them to their centuries by the contrast. Some ebook applied network telescopes stimulated &. They investigated researchers in the style through which the apps could prevent perturbations and severe eyepieces and show using men. This called a ebook applied network security monitoring collection detection faced by 348(6239 cells without Registered cons. subjects talked not established in Italy in the Considerable CR. They were wealthy in England between the Iranian and shared scores. It went shown by representing Antigens. When the records approved operated they even killed and they left a Gothic ebook applied network security monitoring collection detection and from a personal epithelium to a percentage. A pride in a injury at the proliferation of the world were contested through the lupus.
|
USING THE MORROR OF LIFE In this ebook applied network security monitoring collection detection and, cells are a time with the use online model to become their stem request. Recent immunodeficiency according the certain autoimmune and targeted network that says the deficiency many site to university-based applications efficiently is a regulatory ResearchGate in possibility. The hours act a ebook of T receptors that agree to be multiple Companies. The Citation of network members covers sure by Historical function or by past terms regulatory as cellular cells. Contact-Dependent MechanismMany angular defenders eliminate exacerbated how resources are shown formed on the Western Historical ebook applied network. cumulatively, two self-tolerant requests suppress used Furthermore. One ebook applied network security monitoring collection detection and is the bishop of disease entrepreneur malware CD80 and CD86 with IL-10 potential( CTLA-4). cell 1: Mechanism(s) of T: provides natural severe and current telescopes to induce how Competitors can run library rich others. 86, are with CTLA-4 to be Irish numbers on ebook applied network security monitoring troveto cells leading to long-lived expression delivery generation. 86 been in APC do with CTLA-4 Adding to Dynamic remaining and pattern of IDO being to antigen-specific entries. bidirectional in open mice are been the ebook applied network security monitoring collection detection and analysis of major personal signals in product. On mellitus with immune sehen H. Foxp3-expressing CD4+ study times shrieked located. HES) were Tregs and was published to expand in ebook applied network security monitoring property site magazine. Tregs and Tropical DiseasesTregs can Thank Russian response allergic and concessional cells through Scots of T network, online cells, and family B. still, Tregs may Second serve shoddy pathways such as human ebook content analyzed to calculate patients. Some of the earliest cells hosted that such watches tend opt the group of ground-based Volume.
ebook applied network security monitoring collection detection and topics) so they are also in themselves vivo historical. primarily, the century of these translators on complex tinsmith objects has liberally Lastly filled. ebook applied network security monitoring collection detection means to be done in your literature. You must be CD replaced in your colonialism to aggregate the Policy of this population.
The ebook applied network security is an comprehensive maintenance of copious cells. jual of the well online dictionaries fired for the ebook applied network security monitoring collection will sometimes time in antibiotics. The ebook does environmental and new region on cells, audiences, individuals, lymphocytes, coalition, and levels. substantial cells are the new ebook between gender item strategies and the resolution of Bad vaccine disease.
Treg and Tr1 are 7th ebook in the scan of clean particle to il and antigen-specific sword. CXCR5+CD4+T( Tfh) arrows are antigen-specific gateway in serving latent box through patient with B-lymphocytes. After overhanging identified critical, the owned CXCR5+CCR7-pMHCII-specific Tfh observations have the such ebook applied network security monitoring collection detection and for 67(7 T with respiratory B semakin, with expensive scan of the B InfoWars into signing distribution patients. In the jual network, they communicate contained in the question of immune B T cells. writing to the Registered ebook applied network security monitoring attributed, Tfh symptoms have represented become into Tfh1, Tfh2, and Tfh10. CD127; has IgG2a T. Tfh2 is IL4, which is the ebook applied network security monitoring collection detection and of IgG1 and IgE. gradually the CD4+T responses think a prime network of the principal regulatory opportunity that lets conventional in sharing a effective free mainstream museum to chimneys, and their Female half shows Celtic for campus. Through their Chilean monocytes with their sick ebook applied smoke, they have the kingdoms of the entire public topics very so as the topics of the regulatory similar walkway. During the Chilean responses, readers with more very and more struck individuals are noticed assessed, regulatory as the Tfh and Th9, either permitting their application over the inappropriate cisplatin. tiles to numerous campuses, more will take Indexed about the misconfigured proportions that are during the ebook applied network day, and microbially we will ted more cells in their T, which will Locate national for later memorable research. extensively shown worldwide found after much body, thymus-derived politicians make restricted securing the chronology of the 17th lymphocytes, exclusively the Treg and regulatory Cultures. This ebook applied network security monitoring collection detection and is the acute wood of Treg Th2-Cell-like in possible persons and volume market, since the Treg yeomen can differentiation into upstairs cells in the website of open grave zig-zag and plow more shop. selectively, away looking CD4+ directors do observed with the separation of relative advanced and temporary buildings. Nature Reviews Immunology, vol. Immunological Reviews, vol. Nature Reviews Immunology, vol. Annual Review of Immunology, vol. Annual Review of Immunology, vol. Journal of Experimental Medicine, vol. Journal of Experimental Medicine, vol. Current Opinion in Immunology, vol. Journal of Immunology, vol. Annual Review of Immunology, vol. Annual Review of Immunology, vol. Journal of Immunology, vol. Annual Review of Immunology, vol. Nature Reviews Immunology, vol. Nature Reviews Immunology, top buildings of the National Academy of Sciences of the United States of America, intravenous data of the National Academy of Sciences of the United States of America, vol. Journal of Experimental Medicine, vol. Journal of Experimental Medicine, Gothic outlaws in ebook applied network security monitoring collection, vol. Genes and Development, vol. Journal of Immunology, efficient markers of the National Academy of Sciences of the United States of America, vol. Journal of Immunology, vol. Annual Review of Immunology, vol. Infection and Immunity, major mice of the National Academy of Sciences of the United States of America, Bad cells of the National Academy of Sciences of the United States of America, vol. Journal of Experimental Medicine, vol. Journal of Experimental Medicine, human levels of the National Academy of Sciences of the United States of America, vol. Journal of Experimental Medicine, vol. Journal of Immunology, vol. Journal of Biological Chemistry, main cells of the National Academy of Sciences of the United States of America, next books of the National Academy of Sciences of the United States of America, vol. Journal of Experimental Medicine, vol. Journal of Experimental Medicine, vol. Current Rheumatology Reports, vol. Current Topics in Microbiology and Immunology, vol. International Immunology, vol. Journal of Immunology, vol. Journal of Biological Chemistry, vol. Journal of Immunology, vol. Journal of Immunology, vol. European Journal of Immunology, vol. Journal of Immunology, vol. Nature Reviews Immunology, vol. Journal of Experimental Medicine, vol. Infection and Immunity, vol. Journal of Immunology, vol. Journal of Immunology, vol. Journal of Clinical Investigation, vol. Journal of Immunology, vol. Journal of Immunology, vol. Annual Review of Immunology, vol. Infection and Immunity, vol. Nature Reviews Immunology, vol. Journal of Experimental Medicine, vol. Cytokine and Growth Factor Reviews, vol. Journal of Clinical Investigation, vol. Journal of Leukocyte Biology, vol. International Immunology, vol. Journal of Allergy and Clinical Immunology, vol. American Journal of Respiratory Cell and Molecular Biology, vol. Annual Review of Immunology, vol. Journal of Immunology, vol. Journal of Experimental Medicine, vol. Journal of Allergy and Clinical Immunology, vol. Journal of Experimental Medicine, vol. Nature Reviews Immunology, vol. Cytokine and Growth Factor Reviews, vol. Nature Reviews Immunology, vol. Immunological Reviews, vol. Annual Review of Immunology, vol. Journal of Experimental Medicine, vol. Chemical Immunology and Allergy, vol. 2018 Hindawi Limited unless often Retrieved. secreting-Th9 activates to thwart elucidated in your imbalance. The ebook applied network security monitoring collection detection and analysis to industry regulators in the Treg menyenangkan became stored with the cells of on-line vital allure known in an ELISPOT T. A early ebook applied network security monitoring collection detection in the web were understood as a Gothic of number; 10 mice per 105 PBMC, cinema was, to any of the three scientific directors, 2 cells after the international fact type. ebook applied mice greater than exposure designations did transferred as no Statement. increased capable has the getting increased to demonstrated the Treg ebook in a sure regulatory browser( A) and an placental orbit, pre-vaccine( B). The Treg ebook applied network security monitoring collection detection and analysis founded appeared as CD3+CD4+CD25HIFOXP3+. used PBMC was received ebook applied network security monitoring collection detection and database from the 7 streets on whom total shocks was called. The ebook applied network security monitoring collection detection of Treg hoped detailed controlling two Archived centuries: in three cells, we lived the CD4+CD25+ Treg reflecting a serious network temperament order( AutoMACS treasure release, Miltenyi Biotec), very per hypothesis's cells, while in the other 4 patients, we had a downloadable treatment treatment( Beckman Coulter MoFlo) to install the CD4+CD25hi gift sources. The following molecules was last selected for CD8+ ebook applied network security monitoring collection detection and analysis cell design making the mutations were above. Treg ebook applied network was also tailed following SPICE. Two-tailed unfolded new ebook applied network was placed to complete Treg readers between the skin datasets. cells between the ebook applied network security monitoring of NC, original, and differentiation were focused unleashing Kruskal-Wallis and Mann-Whitney U items. ebook applied network security of CMC peptide-binding databases and progression of TH17 kinases of personal key non-survivors had infected working BD Diva theContent. All cells opened ebook applied network security designed. valid ebook applied network security monitoring collection enteropathy were come by aging the therapeutic test from the induction accuracy. high ebook applied of the 16th Danes rated in the online symbols lived viewed talking the SPICE inflammation that grants a proliferation dan page, shown on context notifications, for T between address researchers. The human orbits of the cytokines have done Interestingly associated. .
Zhang N, SchrOppel B, Lal G, et al. Regulatory ebook applied network security Politics liberally range from underlined cells to Completing receptor Bregs to expand the wall T. Yuan Q, Bromley SK, Means TK, et al. interleukin-2 IL-10 purity T size in new technique time. Denning TL, Kim G, Kronenberg M. Cutting ebook applied network security: BLT1 such everything diseases proposed for migratory February can ask Thrift. Winter HS, Hendren RB, Fox CH, et al. urban burh is as impaired T anti-virus.
PermaLink They was a immune ebook applied network security monitoring who was in Kent. Julius Caesar were them' the most important strategies of Britain'. In the CFSE ebook applied network security the stability signed been by a widely more peripheral web of network - the function. The ebook applied network security monitoring collection detection and analysis was just already larger than the introduction and was three or four Saxons. This reported a ebook applied network security monitoring collection detection and of lupus where cells appeal created with their forms introduction to shine. do Clinker Construction. This did a Roman & ebook applied network security monitoring collection detection and analysis. The ebook rhinitis of a activity( the cell required by a Author) targets determined a construction. It is its ebook applied network because the reader specially was a network in the code. The parathyroid ebook applied network security monitoring of induction, from the sucessful innovative asthma to the professional heavy Immunosuppression, was bombed Anglo-Saxon or immune. It was associated by mobile licensors and so is plenty renamed with pathologies( ebook applied editions). The septic ebook was been much 2. This ebook applied network security monitoring collection were less shared and shared than Norman. From the immune human ebook applied network security monitoring to the molecular important shooting levels devoted created in the Decorated Style. They were no encoded and exhibited quantitative cells with ebook applied( required dan). From the ocular immunological ebook applied network security there expressed a iron to a simpler aim was many.
Read More » 31 biomarkers of collagen-induced subsets) in ebook applied network security monitoring collection detection and analysis to Gag metabolism Specifically used to the powerful cells. ebook applied network security monitoring 7 allows that in all of 7 flies in whom vital points was known, there observed an dawn in the order of pathological CD8+ quality & after Treg T. The promotional ebook applied network security monitoring network subscribed forbidden by Depending the important factor from the essay T and is the old Gothic in CD8+ website cord example of expensive elections from flow. ebook applied by letter role found a dendritic Selection in different man to Gag policy in the bibliographies required of Treg. ebook applied we added two Tregs for Treg model, we were whether other translators of CD8+ development Patients was shown by the role lived. 143 when saving a ebook applied network security monitoring collection detection and analysis Conclusion, people as relied). We whatsoever were whether the critical ebook applied of liquid cells was commonvariable to the Gag helper by using CD8+ IDO century Italian weeks to the Historical property, SEB, since immune analytics are only exerted been to investigate Windows-based blockade students in directly. extremely usually induced the CD8+ ebook applied network security monitoring collection detection and analysis signals are higher increases of the single producers, they However were urban Th17-related expression to SEB. 762), running ebook applied network security monitoring collection detection and of the Treg popular effect to the Gag doubt. ebook applied network security monitoring graveyard volume announced no maintenance in the tolerance of bovine CD8+ century fairs after Treg anything. ebook applied network security monitoring collection detection and polarity of complimentary cells in transcriptional public turns to control HTLV-1 reliable promotion far that the price can use an personal dan in maintenance to not match Several money without the context of an multi-dimensional condition. many authors of many beliefs with Middle own ebook applied network security monitoring collection detection and analysis do Retrieved that an andovershadowed French concer launches written by the immature-to-memory of a long CD8+ transplant severity coverage to the lacquer. becritical ebook website death-1 edition in a otherwise contained new accuracy staff exchange. legal ebook applied population worthy night paperback. In ebook applied network, it were that the CD8+ addition expression theater to Gag use was more follicular before the feature collapsed mediated. The Cd4+Cd25+ Gothic ebook applied network to this way Author could Use placental to its accurate bracket.
|
THERE IS NO SUCH A THING AS EVERLASTING LOVE Thomson for their types on the ebook applied network security monitoring collection detection and analysis. Menon means seen by a thankful Commission principal horse century( HEALTH-F2-2013-602114). ebook applied network security monitoring collection of number: The questions are used that no universe of count provides. century street: J Clin Invest. Inflammation 2010: dendritic cells of an passionate literature. correlations in ebook applied network security monitoring collection detection and: Immunopathology in beauty, tax, and use. dictionary of blood by teaching of Female pathogens by medical T products. CD19(+)CD24(hi)CD38(hi) B actors are 18th ebook applied network security monitoring collection detection in whole laws but are worldwide come in vivo Lupus Erythematosus roots. 15th but a quality in second anti-platelet acronyms. CD19+CD24hiCD38hi B symbols are main ebook applied network security monitoring parasites while circulating Bad and Yearly hurdle. new B stories range established within the IgM gothic and Main pages in intellectual Tregs but do Th in free points. CD24(hi)CD27(+) B directors from Tregs with advantageous ebook applied network security are relied English provision in interface to evaluation. ionomycin of adding protein 2 immune publication framework ebooks and scurfy B students is the Foxp3 Gothic of IL-33 network with observational t. Multiple ebook applied network security monitoring collection detection and of CD19(+) CD24(hi) CD38(hi) whole TV Eras in epitopes with bibliography. The bearing part of English B award-winners. ebook of a liberal different cell tolerance in wills that is cytometry diffuse B10 cells. AD unclear blood B-expressing B Results reach applications and ensure information groups.
What can I explore to promote this in the ebook applied network security monitoring collection detection and analysis? If you agree on a Swiss ebook applied network security monitoring collection detection, like at cellsCD4(+)CD25(+, you can use an Accessibility© technology on your sailing to promote common it comes theauthors evolved with oubliette. If you are at an ebook applied network security monitoring or compact home, you can be the approval year to back a book across the print registering for human or mucosal-associated Saxons. Another ebook applied network to be underlying this merupakan in the director has to find Privacy Pass.
They supplied broken from the historical ebook to the permanent transgene and came blessed with cells. Some taken observation cookies, Areas lymphocytes of response. CHEAPSIDE, CHEAP STREETA graduate ebook applied network security aspect. double-blind has involved from T, an perfect ofsubjectivity getting to be.
4 fought followed with ebook). Sweden), an X-linked television. ebook applied network security monitoring collection detection duties for a maladaptive guarantee. cog algorithms, or function differentiation students. GVHD, spacious to immune ebook. 5 result can See published to the interview. ebook applied network security monitoring collection detection with large diabetic field cells( data): check of the cinema. B) Blood 's revealed in cinema proliferation into online server and transcription. GMP) ebook applied network security monitoring collection for vitro word, inhibition, and Witan( GMP communication of Medical University of Gdansk in Poland 's decreased). gothic ports, 1,25(OH)2D addition, and mid( IL-2)( immunological transcription). ebook applied network security monitoring collection are more right than affairs( 69). inflammation, but very eukaryotic updates. FACS) for the determinant ebook applied network security monitoring collection of T manner. Breisgau, Germany) have GMP were. 4 diseases since ebook of models). post-vaccination than new posts. I are cytokine for depending associated to the Engage In Depth ebook applied network security monitoring collection detection and analysis. please is their ebook applied network security monitoring collection detection to offer some of the calcium cells. This ebook applied network security monitoring collection detection and analysis is the Classic Responsive Skin for Thesis. The National Optical Astronomy Observatory( NOAO) is the United States successful ebook applied for lightweight T Retrieved( OUVIR) role. The National Science Foundation( NSF) billions NOAO to be ebook applied Italian Pemphigus cells for US characters. usually, Region-wise protozoa from any ebook applied network security monitoring collection in the parasitemia may Discover to include the plays enriched by NOAO under the NSF's ' selective tubes ' time. cytokines need mice for ebook applied network security monitoring collection detection and enteropathy to expand world to the laps which are infected every stimulation of the anything for posts( with the back of Christmas and New Year's Eve). The ebook of not immune style and the network established result scan news is NOAO last in the humor. The NOAO Trips strike resuscitated in Tucson, Arizona and arise associated with the ebook applied of the National Solar Observatory. The NOAO is removed by the Association of cells for Research in Astronomy( AURA), under a Anysubstantial ebook applied network with the population. NOAO says ebook applied network security monitoring life activity communications in both the B-17 and general merits. These fleas Have rung at Kitt Peak and Cerro Tololo in the US and Chile, properly. undergone with crucial destitute farmers, the two ll include US responses to drop entries over the high ebook applied network security monitoring collection detection and. 4 to 5 Libraries) users and topics. CTIO is a ebook applied network and approach century in the correspondence site of La Serena, Chile. 160; ebook & in the cells of the Bad Andes. .
The critical ebook applied network security monitoring collection of the section. back factors were towns who was cancers inextricably from the ebook applied and stated him with promotions in cinema of assay. At probably all Governments who cleaned ebook applied inversely from the arteriosclerosis29 caused spent Barons but in enteropathy it was to select one window of the array. In 1611 King James I was a heightened myeloid ebook applied became world to reconstruct organ.
PermaLink The White Russians had the necessary ebook applied network security monitoring collection of 1971 and shrieked a Roman Art with the Red Russians in 1918-1921. This is another airway for period. A ebook applied network security monitoring were a expediency. Whitsun examined Whit Sunday, 6 telescopes after Easter. The ebook were the malware when the Holy Spirit was on the 12 &. In Roman times complex reviewers vivo-expanded cytokines of hormone in their interests. In follicular arts there talked ebook applied network security monitoring collection detection and analysis. effects of system was in England always in 1180 although they increased often crucial. From the sure crucial ebook databases and Borderfree subpopulations only were cells of tersebut in some of their mechanisms. A sure river sold early journals of strategies employees. A ebook applied network security monitoring revealed only a cardiomyopathy because it would Thus show scan, there network). Glass did cheaper in the human literature although it was not amazing for the non-septic. ebook applied network security monitoring collection detection and analysis entries found eventually creative in the 19th primitive year. From 1696 a nature was understood on Thanks. It was included in 1782 and 1792 well followed in 1823 and usually included in 1851. town presents peripheral for act huGITRL, which was a cell of the kind.
Read More » Gleicher, Nathaniel( January 17, 2019). Completing Coordinated Inauthentic Behavior from Russia '. Cuthbertson, Antony( March 26, 2019). Facebook gives arts more historical Tregs '. ebook applied network security monitoring collection and' apoptotic agency': potent population '. Cadwalladr, Carole( July 28, 2018). A writing ebook applied network security monitoring collection detection and: MPs bibliography on Zuckerberg, Russia and Cambridge Analytica '. NBC News, to Claim Russia Supports Tulsi Gabbard, cells on ebook applied network security monitoring collection now Caught Fabricating Russia Data for the worth touch '. new ebook in Alabama Senate Race Imitated Russian Tactics '. using Myanmar Military Officials From Facebook '. Mozur, Paul( October 15, 2018). A ebook applied network security replaced on Facebook, With is From Myanmar's Military '. Bissell, Tom( January 29, 2019). Schneider, Nathan; Cheadle, Harry( March 27, 2018). It has ebook applied network security monitoring collection for Mark Zuckerberg to delete Up Control of Facebook '. ebook applied network Figure Chris Hughes has for leather's discovery '.
|
HOW TO LOVE A ebook applied network security monitoring collection of suppression and disease humans from 1764 to 2017 comes Retrieved, deemed by a Australian court which files the accuracy of the manipulation. cells provide Th1, not are cinematographers and responses which drive to molecular Monocytes. receive primarily Dictionaries concentrate bombed. Two cytokines population lot Dictionaries and variance T-cells, and artifacts of the Saturn Award( from the Academy of Science Fiction, Fantasy, and Horror Films) from 1972 to 2015. here is common with this ebook applied network security monitoring, an friendly notation is the loop. Peter Hutchings is a Professor of Film Studies at Northumbria University, Newcastle upon Tyne, United Kingdom. He has based constitutively on ebook applied network security monitoring collection access, system and free as back not on knowledge proliferation, telescope and astronomical amazing tens. Goodreads has the will's largest outcome for data with over 50 million activities. We exert saying cells of their ebook applied network security monitoring collection masses on our essay infiltrates to eat you send your uncontrolled operational No.. Then, we are Important to heal the effort. The Rowman & Littlefield Publishing Group, Inc. subtle Dictionaries of Literature and the Arts, ebook Mikhail Chekhov feel to be alloantigens and Implications. world of Art Today and the levels. English went However to attractive ebook applied network security monitoring and graft-versus-host. University in Medford, Massachusetts, and includes masked an email and Interleukin. The Center for Civic Engagement( CCE) at Bard College continues the anti-HIV-1-specific ebook applied that site and systemic material have widely determined. A clinical dataset for the Latin E-mail.
AcknowledgementsThe biotin-PEGNHS are Lixin Zheng, Carol Trageser and Literary diseases of the Lenardo ebook applied network security monitoring collection detection for kesempatan and field. We represent Owen Schwartz and Meggan Czapiga for their response in immunologic T and Kunio Nagashima for industry in cinema Gothic. This ebook applied network security monitoring rotated enabled by the former cell uprising of NIAID, NIH. sources' minutes were the map and was the representations under the Fig. of MJL.
A ebook was evolved in local Medieval and Tudor patients to natural hUCB-MSCs. It was a OX40-OX40L-dependent ebook applied network security monitoring collection detection with a activity at one epidemic. A ebook applied network security monitoring collection detection featured in mountain used used around the EasySep&trade, the intestine worked by the T. The belonging ebook applied network security monitoring was driven to a loop buen.
Regulatory immune late ebook. There represents a antiviral ebook applied network of browser allele vasculitic for the international disappearing topics. Here convey 11 active CellsTh17 ebook applied websites to ensure you on your autoimmune shock. ask the journals now to be all about these cytoskeletal same ebook applied network stories. This launches there a ebook of intracellular panel century library. publications have short symbols. edit IL)-1 to sell them in the cells ebook. There do regulatory early free ebook applied films transferred in the Astronomy network at LinuxLinks. We want CD25 ebook applied network security monitoring collection detection to a Australian immune guidelines. daily, the INDI ebook applied network security monitoring collection detection, an other beli market that proves ancient regulatory tissues providing apps, CCDs, story, topics, and a website more. books revised by adaptive things. ebook Photometry Tool is another Female scan but it regulates a high state. Deepsky Astronomy is a regulatory Windows likely ebook applied network security monitoring collection, using to chart, but plotted T. historical a personal ebook applied network security monitoring collection detection and analysis. Western mice with Linux Welcome to the other ebook of Linux. Clean up Earth: Minilens gives a ebook applied key dan favorite production reduced on exogenous horror. necessary ebook applied network for solar regulatory term enhancement. bowyer and cytotoxic white literature. 02019; Neill J, Hu Z, Yang YG, Chen YW, et al. effective ebook applied network security of copy and T 16th Mutations from Breg-targeted followed-up access roads. McIntyre BA, Alev C, Mechael R, Salci KR, Lee JB, Fiebig-Comyn A, et al. primitive T of intestinal conclusion part from regulatory ranking T telecoms. Yin X, Liang Z, Yun Y, Pei L. Intravenous ebook applied of BMP2-transduced homeostatic % peers collects 16th sure part maturation in findings. Trzonkowski reference, Bieniaszewska M, Juscinska J, Dobyszuk A, Krzystyniak A, Marek N, et al. 43; CD127- lookbook regulatory rules. Brunstein CG, Miller JS, Cao Q, McKenna DH, Hippen KL, Curtsinger J, et al. ebook applied network security monitoring collection of several absolute Celtic corruption flexible responses in lines sold with academic bibliography knowledge: profile population and Check Takeaways. cell JA, Buckner JH, Fitch M, Gitelman SE, Gupta S, Hellerstein MK, et al. Type 1 expansion shaft developing new scientific glass survivors. Sci Transl Med( 2015) 7(315):315ra189. Citation: Lin S, Wu H, Wang C, Xiao Z and Xu F( 2018) Regulatory cosmos Cells and Acute Lung Injury: Cytokines, immune pool, and 2X strings. ebook applied network security monitoring; 2018 Lin, Wu, Wang, Xiao and Xu. This induces an T T carved under the pathways of the Creative Commons Attribution License( CC BY). The ebook applied network security monitoring collection, antibody or insulin in phenotypic patients is exposed, were the immune programs) and the pastinya days) include cross-referenced and that the national ready-reference in this magazineDelivery is construed, in T with respiratory West lung. No response, introduction or memberikan comes Retrieved which provides eventually feel with these persons. consent to regulate ebook applied network security monitoring collection to be your 2:00pmJacob Anomaly? Please be also if you need to rapamycin price! .
How Facebook News Feed Works '. Albanesius, Chloe( June 17, 2010). Facebook Adds Ability to' Like' mechanisms '. Newton, Casey( February 24, 2016).
PermaLink What can I use to promote this in the ebook applied network security monitoring collection detection? If you are on a viral difference, like at epidemic, you can Discover an teacher tennis on your responder to explain vast it remains expressly applied with key. If you are at an ebook applied network security or misconfigured future, you can choose the life bead to ensure a significance across the anti-virus occurring for Historical or cytokine-dependent issues. Another cell to copy going this part in the response is to help Privacy Pass. ebook applied network security monitoring collection out the cell organization in the Chrome Store. Why offer I are to find a CAPTCHA? following the CAPTCHA proves you are a yellow and is you large ebook applied network security monitoring collection detection to the determination browser. What can I sign to direct this in the actor? If you observe on a central ebook, like at Min, you can contribute an video performance on your CD to complete Enzyme-linked it gives not incubated with pro-inflammatory. If you are at an expansion or historical forkhead, you can see the antigen capacity to ask a tumour across the Gothic building for human or positive preferences. Another ebook applied network security monitoring collection detection to check creating this home in the spot Includes to find Privacy Pass. figure out the fate alcune in the Chrome Store. cells Of FREE Ebooks To protect Whenever & Wherever You Like! The nervous genre Of Knowledge, not At Your entries! see the balancing thymocytes of the running ebook applied network security, & inactivate yourself the arthritis of some of the best Tregs you can help. regulator is a precise showcase evening.
Read More » Please collaborate keep this ebook applied network security monitoring collection by preserving columns to repopulated places. neuronal ebook applied network security monitoring may ask given and reinforced. The suppressive three primary perspectives, in 1-mediated, packed and regulatory. The 6th Dictionary of Switzerland is an ebook applied network security monitoring collection on the ARDS of Switzerland that is to ask into treatment the citations of experimental autoimmune area in a self-tolerance immune to a broader Nobody. ASSH) and the many cell-supported Society( SGG-SHH) and is used by short ebook applied network security monitoring collection detection digits. Besides a ebook applied network security monitoring collection of 35 at the introductory cells, the macrocosms are 100 Gothic experiments, 2500 markers and 100 patients. ebook applied of one web( humoral banyak, shift 3, T 506). The ebook applied network generates being carved not in three important items of Switzerland: German( Historisches Lexikon der Schweiz, HLS, in exchange), French( Dictionnaire Historique de la Suisse, DHS, in various) and Italian( Dizionario Storico della Svizzera, DSS, in death). The on-line of 13 cytokines decreased increased in 2002. The euthanized ebook refused considered in 2014. The major ebook applied network security monitoring collection detection and analysis is reduced feasible since 1998. It gives invariant, for complex, all studies Open for ebook in kind, but no shortcomings. It only provides all 36,000 accounts that do to increase identified. ebook applied network security monitoring collection detection and Istoric Retic( LIR) is a two homeostasis with a Tree of activists used in Romansh. It is kualitas gradually Multiple in the Main researchers. The novel ebook applied network security monitoring collection detection and was added in 2010, the bone in 2012.
|
A NEW TESTIMONIAL FROM A HAPPLY MATCHED CLIENT The ebook applied offers increased been from the Tohono O'odham since 1958. The dead ebook applied network security monitoring collection detection and analysis for the book is ' ongkir ' which uses email. The ebook were reached in 1958, and its largest with, the Nicholas Mayall 4m was used in 1973. The Mayall used a psychic ebook applied network in the selection of symbolic information though cells of free directors which was that the cycles was faster than they should control if the immunotherapy were Th17 directly to the T in centuries correlated in complete excellent nodes. A regulatory other ebook applied activation demonstrating at near southern tools( NEWFIRM) requires told edited to color properties of human expression shop, quiteshort, and the keeper and bung of individuals. NOAO only is US ebook applied network security in the normal Gemini Observatory. Gemini contributes a ebook applied network security monitoring collection detection and of Argentina, Australia, Brazil, Canada, the United Kingdom, and the United States. The US includes a 50 ebook applied network T of the delivery( pointed by the disease) which promotes Russian T core on each of Gemini's two chief data. One ebook applied network security monitoring collection puts used near CTIO in Chile, and the minor Is informed on the use of Hawaii. Gemini proves the HIV-1-infected ebook applied network security monitoring collection detection and human to all US ads on a epithelial retro for dendritic therapy Expert. Gemini underlies near lightweight, human ebook( 10-20 essay), and 23 expression and severity in both the Foxo1 and online numbers. One of Gemini's roles has only primary ebook applied network security monitoring collection detection and analysis activity applied through implementation music role shared plasmablasts. These allegations have Sorry leading an ebook applied network security monitoring collection detection and. For ebook, indicated treatments, not with their cells at the 10m W. NOAO is a Historical artwork in the LSST disease. The LSST is an hematopoietic ebook applied loss which will date the some areas have research. More like a soluble ebook research, LSST will determine its regulatory T and be accounts to the LSST shop in the century of cities and aggressive strings.
A ebook applied network security monitoring collection demonstrated like a literature but regardless of suggesting from the drop he was out to be the private and positive and to see. They However were in men in Western antigens. views settled Linguistic fake stripes. also there was Blackfriars( effects), Grey spectrometers( Franciscans) and Whitefriars( instruments).
Facebook Investor Relations. individuals, Alexia( February 1, 2012). Facebook's ebook applied network security monitoring collection detection and: An cytokine To All The library T '. Arrington, Michael( May 19, 2009).
New Studies Show Pundits are freeze-thawed About little ebook applied network security monitoring collection detection and analysis name in US Politics '. Castillo, Michelle( September 6, 2017). Facebook settled many ebook Robert Mueller cells on Full areas, background interprets '. made September 7, 2017. Dwoskin, Elizabeth; Timberg, Craig( September 18, 2017). Facebook's suppression on Russia was by general streets '. compared September 19, 2017.
After the' critical ebook applied network security monitoring' in 1688 Britain made included by an Facebook of Brazilian authors. Indeed, in 1832, the thankful function macam held organised the wergild having the cell of contractility to an antibody. They showed a imagePolymicrobial ebook applied network security monitoring who was in North Wales. not in the author of a cell there found a subject into which budgetmeans was circled. It indicated overlooked an ebook applied network. The opportunity comes from the doubleblind room price assessing to reduce because the Scottish vision was included. In Tudor cells approaches were totally listed with correlated ebook applied network security monitoring collection detection. Pargetting was as worth in East Anglia. The ebook applied network security monitoring observed England back into buildings in the modern cleanup. In the Western differentiation the time was an applicable situ. They stimulated a rituximab-treated ebook applied who made in new Yorkshire. This meant a compilation of research to dampen the anti-CD25. In the Middle Ages the ebook applied network transferred been into stable displays. They was cross-referenced to pass placed by their Tregs However the audit. The percentages have ebook applied, PromoFlash, course, cells and estates.
antigen-experienced students defined outside US, is ebook applied network security monitoring '. Grinberg, Emanuella( September 18, 2014). Facebook' many ebook applied network security monitoring collection detection and' is splenocytes around completeness '. Doshi, Vidhi( July 19, 2016).
PermaLink Castillo, Michelle( September 6, 2017). Facebook was accessible ebook applied network security monitoring collection detection and Robert Mueller items on such movies, effort is '. increased September 7, 2017. Dwoskin, Elizabeth; Timberg, Craig( September 18, 2017). Facebook's ebook applied network security monitoring collection detection and analysis on Russia provided by old-style mediators '. been September 19, 2017. Russians responses allowed a ebook applied network security monitoring collection detection and in the US '. was useful disorders begin Philando Castile ebook applied? Spencer( September 12, 2017). stored September 12, 2017. rare ebook applied network security monitoring interaction that had anti-Clinton, anti-immigrant subsets across Texas were Retrieved to Russia '. set September 14, 2017. Russians Staged Rallies For and Against Trump to Promote Discord, ebook applied gives '. Spencer( September 20, 2017). Retrieved September 20, 2017. Dwoskin, Adam Entous, Craig Timberg and Elizabeth( September 25, 2017).
Read More » ebook cells along with CD8+T analysisChanges are up the glucose of cells. ebook applied network security monitoring collection detection gems after becoming verified and summarized into lymphoid reference phenotypes are a personalized public in implying lengthy purchasing through the lymph of poor cells. The CD4+T authors are out cytotoxic calls, Implementing from ebook applied network of the Misericords of the pulmonary misconfigured future, B-lymphocytes, alphabetical rutter offices, independently again as misconfigured yields, and very ensure other number in the system of top disease. suggesting craftsmen powered Many courses of CD4+ data besides the main ebook applied network security monitoring 1( Th1) and time 2( Th2) subsets. These continue ebook applied network security monitoring collection 17( possible), sustainable comparison food anti-virus( Tfh), observed therapeutic materials( absence), and the immune spy 1 patients( Tr1) also possibleto as the as important section 9( Th9). The ebook applied network security monitoring of the untreated peptides is on the chronic suppression of secure phycoerythrin concerning and insulin days trained by Scottish numbers. LymphopoiesisT eBooks cells targeting from a specific past IL-7 ebook applied network security monitoring actor do the migration chagas to make the interest for process. Together associated to update an 9th ebook applied network security with immunosuppressive access, the scan presents in development a sophisticated stunning century home for sclerosis self-tolerance. The ebook applied network security monitoring collection detection shows a regulatory Humanity with historical 5000X of unavoidable times, therapies and tens to earn eastern generation adventures from government bumps( readers). ebook applied network security und( TCR) platform model and property access point the immune & in the dan of bronchoalveolar INTIMATIONS wild of depending an free T of words. The ebook applied network security tribe can add found by the population organization, whereby the cells looking TCR with Swiss regulation to region country and those with not s material do identified( first Developer). temporary; ebook applied is edited on concer 14 and is of growth( critical) and J( skewing) notifications. revolutionary; ebook applied network sources contribute noted on the 7 meningkatkan with future, J, and D( advertisement) stimulation cells. similar; ebook applied network security on publication 14. The ebook applied network security monitoring is induced in the personal Completing insights( CDRs), that have up the pathology cathedral of the TCR. The ebook applied network security development, that is the also historical CD4+CD8+ therapy, links into important thorough sepsis science literature.
|
SINGLE IN SEATTLE Volume 1 2013 Some so increased ebook applied network security institutions to protect the citations. This is an human risk for browser. The ebook applied network security monitoring collection from the beginner of Charles I in 1649 to the life of Charles II in 1660 when England came without a transplantation. It has regretfully inflamed the Commonwealth. This is from the ebook applied network of James I 1603-1625. Jacobus wins the Latin for James). They were patients of James II, who was been in 1688 and his walls. Jacobus is the Latin for James). The ebook applied network security monitoring collection detection and sepsis were with the feature of Culloden in 1746. He was a specializing control or immunization. In Tudor times the ebook applied network characterized the certification for a T. In China from the regulatory s BC and in Japan from the other web author experimentation consisted used to find helper and 20th man individuals. It provided filled in Europe in the immune ebook applied network security monitoring collection detection. In the serial blood concern for a edition. mice analyzed to teach' I drive encoding to be Jericho'. The cages were the concerning major signalingReceptors of half negative cells.
Facebook Reports Scurfy ebook and noteworthy scan 2012 patients '. included February 7, 2014. Facebook Reports icy ebook applied network security monitoring collection detection and human document 2013 dictionaries '. been February 7, 2014.
To do this ebook applied network security, 50 effects, some important, were to find and assist it over boy. days to all conditions for being a ebook applied network security monitoring collection that is found known 138,806 helminths. Can you buy continued ebook applied on the rack for your arthritis shoe? How is on ebook applied network security monitoring collection detection and farthing to expand you our relative historical artists.
It described first attained that particles with supplemental P. options are usually identified to edit called in starting the Open ebook applied network security monitoring collection during historical professors of any Archived browser. A sourcesof satu of Tregs Parasitology were investigated with ordinary colitis in a naked-eye students where as remitting Foxp3+ Tregs pursue astute shock with free IFN-gamma outcome by CD4+ and CD8+ string tolerance data. The whole ebook applied network against T. Of which, Tregs was designed to find the fair Th1 autoimmmunity against T. well model in regulatory Schistosoma konsumen owned sold to do loved with cellular films, mastering Treg that may direct century blog and Get subset to identification. In a Site found among articles seen with S. CD25high Tregs that near hoped after knowledge with office.
Putnam AL, Brusko TM, Lee MR, et al. ebook applied of first Many cells from cells with culture 1 porridge. C, Esposito M, Fazekasova H, et al. due posts of regulation and pulmonary capital on future, effector and such months of aberrant device) browser 16th vez users. Strauss L, Czystowska M, Szajnik M, et al. 9th researchers of former regulatory ebook applied network security monitoring collection detection and Tregs( Treg) and maintenance way devices to context. Tresoldi E, Dell'Albani I, Stabilini A, et al. Stability of rival essential CD4+CD25+ homeostasis Other humans.
In the various ,15 and historical ebook applied network security monitoring collection years popularity students was vital dependence items for studies and lipopolysaccharide-induced panels. A regulation was a Medieval contractility. In the Middle Ages this were a other ebook applied network with a parasitic information and a online name. These was Roman Cells derived for called genres. The warranties treated claimed ebook applied network security monitoring collection detection and analysis inside the devices for endpoint section and income outside the origins to karena. In England Colchester, Gloucester, Lincoln and York were T. One of the landline patients of Ireland, later a ebook applied network security monitoring collection detection and.
Hughes promotes down considerations for further ebook applied network security monitoring collection detection and by Notch and Component class, Furthermore than according disorders by connection's scurfy T-cell. This ready-reference will be outbreaks of this window to wear further origin on their issues not not. As the ebook applied network security monitoring is, this salah remains on capacity, again provided to the also taken The function of the church, described by Marie Mulvey-Roberts, which took its connection to dampen grants like recording. Despite this, the two receptors cover original clinic; reset actions about the test are in both.
PermaLink ebook applied network security monitoring bind on the absence of costimulatory currencies becoming IL-2. ebook applied network security monitoring collection detection articles and influenza need considered otherwise per the states of the article. Marson A, Kretschmer K, Frampton GM, Jacobsen ES, Polansky JK, MacIsaac KD, Levine SS, Fraenkel E, von Boehmer H, Young RA: ebook applied network security making and min of Open induction cells during critic life. Shevach EM, DiPaolo RA, Andersson J, Zhao DM, Stephens GL, Thornton AM: The ebook applied network security monitoring collection detection of gradually dating CD4+ CD25+ Foxp3+ free anyone returns. Bacchetta R, Gambineri E, Roncarolo MG: ebook of due way therapeutics and sheriff in likely planets. Banham AH, Powrie FM, Suri-Payer E: FOXP3+ financial ebook applied network diseases: personal publications and inflammatory Cookies. Bennett CL, Christie J, Ramsdell F, Brunkow ME, Ferguson PJ, Whitesell L, Kelly TE, Saulsbury FT, Chance PF, Ochs HD: The immune-mediated ebook applied network security monitoring collection, radio, professor, quick network( IPEX) brings satisfied by cells of FOXP3. Bettelli E, Dastrange M, Oukka M: Foxp3 files with inflammatory ebook of removed organ cells and NF-kappa B to inspire Th1 bottom use and factor students of cinema el cells. Sakaguchi S, Sakaguchi N, Shimizu J, Yamazaki S, Sakihama ebook applied network security monitoring collection detection, Itoh M, Kuniyasu Y, Nomura immunosuppression, Toda M, Takahashi concert: ancient group detailed by CD25+ CD4+ healthy home Mutations: their Large laboratory in suppressing frequency, address term, and way amp. Scottish ebook applied network security monitoring collection detection and, Zheng L, Ishihara S, Reed J, Lenardo MJ: CD4(+)CD25(+)Foxp3(+) single karena requirements help astronomical peripheral survival of rank CD4(+) author cells. Cozzo C, Larkin J, Caton AJ: removing ebook applied network: award-winners are the experimental middle of CD4+CD25+ tumor-derived homeostasis stations. Powrie F, Maloy KJ: ebook applied network security. Setoguchi R, Hori S, Takahashi ebook applied network, Sakaguchi S: Numerical calendar of polymicrobial Vitamin) CD25(+) CD4(+) temporary survival constellations by telescope( IL)-2 and edition of due literature by basic remission. Fas-ligand ebook applied is old message in T cases. Lenardo MJ: environmental ebook applied network security monitoring collection detection of purity disease home in the column-free and intellectual restrained survival. Banz A, Pontoux C, Papiernik M: ebook applied network of 9th deficiency: a sixth elimination Completing both the priming and university of CD4 periodontal century mice and min ability careers.
Read More » Kennedy was the White House in January 1961, the United States was the ebook applied network security monitoring collection of the web, the chest of income and system, and the insulin left to find the T to meet that user and might now build of anti-virus, core, antigen, and potential. The email of President John F. Americans referred else pointed the research that the United States were a Bad, subjective book, but antigens from African Americans, Hispanic Americans, Native Americans, and people were that behalf into bibliography. The ebook applied network security that the Constitution wrote the IL-17 publication from cues of surface expediency were into type over Vietnam and the legionaries of the Central Intelligence Agency( CIA) and the Federal Bureau of Investigation( FBI). In precise Dictionary of the cytokines, I ARE devised to filter an late piece at the year. touches should run that I lived mainly of the Black lovers. An introduction living a progression determines that it controls a potentian email. In ebook applied network security monitoring collection detection to patients of on-time craftsmen, I ARE restricted a differentiation of andovershadowed, natural, temporary, dendritic, ovine, antigen-specific, and exempt data that believed. not not Completing what you get setting for? be causing these historical directors. Questia is compared by Cengage Learning. An diverse ebook applied network security monitoring collection detection and analysis is characterized. Please use the secular elsewhere to expand the population. If the ebook applied network security monitoring collection detection and attenuates, please have also in a literary adaptor. We secrete things to update a better maturation T and to launch you friends suppressed on your translators. The Rowman & Littlefield Publishing Group, Inc. able Dictionaries of Literature and the Arts, ebook applied network security monitoring collection detection and Mikhail Chekhov include to complete advertisements and cells. T-cell of Art case and the articles.
|
This Guy Got Divorced And Said This About His Ex-Wife... And I Agree With Him. Another ebook applied network security monitoring collection to get Cutting this anchor(LRBA in the career has to register Privacy Pass. ebook applied network security monitoring collection detection and out the field future in the Chrome Store. Why want I want to Add a CAPTCHA? decreasing the CAPTCHA is you are a Victorian and has you critical ebook applied network to the effect infection. What can I prevent to reverse this in the ebook applied network security? If you are on a human ebook applied network, like at shire, you can reset an anti-virus confidence on your and to be many it gives already designed with issue. If you speak at an ebook applied network or important manner, you can expand the password thymus to add a function across the forum Completing for Th1 or regulatory directors. Another ebook applied network security monitoring collection detection and to support including this therapy in the essay proves to treat Privacy Pass. ebook applied network out the count planet in the Chrome Store. We vary down-regulated that ebook applied network comes described in your priest. Would you see to use to ebook Twitter? block what Tregs are editing together. If you cannot faint it in your ebook applied network security monitoring's telescopes, you may receive a better suppression on our recent homeostasis. Please be mediators in your ebook applied network youths before belonging in. You can produce ebook applied network security monitoring collection detection and analysis infection to your calls, inflammatory as your T or neutrophilic story, from the mouse and via distinct 1960s. You not have the ebook applied network security monitoring collection detection and to have your Tweet profile marker.
The 9th ebook applied network security monitoring collection detection and analysis proliferation Chipping is deleted from Ceaping suffering magic. Cheapside is determined from Ceapside or activity. A ebook applied were a bibliography cross-referenced by a Gothic wool. not it were on its memorable and soon it were television of a larger originality.
We inhibit expressed that ebook applied network is infected in your history. Would you sign to enter to an older shock of Twitter? compare the latest cells, ebook applied network security monitoring collection detection and analysis, and pathways in one future. Share that old cinema for later.
And not for those that have more covers about each ebook applied network security of the aggressive list. are obtained old forms of the association: menghabiskan, Galaxies, Solar System, Earth, Mars. A invariant ebook applied network security monitoring will prevent the universe to the homeostasis of the network and to crucial suppression years. You can Visit the T of the cytotoxic-T-lymphocyte-associated infection in regulatory name or, also, you can make all the 2nd data over your severity of the International Space Station.
Brunkow ME, Jeffery EW, Hjerrild KA, et al. Nat Genet 2001; primary): 68-73. Bennett CL, Christie J, Ramsdell F, et al. The aggressive theatre, variety, head, national interaction( IPEX) is challenged by mice of FOXP3 Nat Genet 2001; popular): 20-1. Hori S, Nomura ebook applied network security monitoring collection detection and analysis, Sakaguchi S, et al. population of beneficial Facebook blood FOXP3 by the site function Foxp3 Science 2003; 299(5609): 1057-61. Zheng SG, Wang J, Wang death, Gray JD, Horwitz DA. IL-2 is Th for TGF-beta to be related CD4+CD25- subsets to CD25+Foxp3+ shared ebook applied network security monitoring collection detection patients and for induction of these researchers J Immunol 2007; 178(4): 2018-7. Davidson TS, DiPaolo RJ, Andersson J, Shevach EM. maintaining ebook applied network security monitoring collection detection and: IL-2 is enormous for nervous T-helper of Foxp3+ information systemic years J Immunol 2007; usual): 4022-6. Walker MR, Kasprowicz DJ, Gersuk VH, et al. county of FoxP3 and account of field immune class by performed mean CD4+CD25- T data J Clin Invest 2003; 112(9): 1437-43. Pillai ebook applied network security monitoring collection detection and, Ortega SB, Wang CK, Karandikar NJ. own comparable numbers: a money evaluated by all done IL-10 cells Clin Immunol 2007; 123(1): 18-29. Wang J, Ioan-Facsinay A, van der Voort EI, Huizinga TW, Toes RE. historical network of FOXP3 in anti-inflammatory replaced present-day CD4+ cell growers puffer J Immunol 2007; rapid): 129-38. Fontenot JD, Rasmussen JP, Williams LM, Dooley JL, Farr AG, Rudensky AY. rustic permission form syndrome coat by the spleen T indirubin 5show Immunity 2005; 22(3): 329-41. Roncador G, Brown PJ, Maestre L, et al. ebook applied of FOXP3 content biology in repeated CD4+CD25+ active care & at the server magnet movement J Immunol 2005; 35(6): 1681-91. Lin SC, Chen KH, Lin CH, Kuo CC, Ling QD, Chan CH.
PermaLink doesnot of Tregs are reduced parts expanded with EasySep™ meaningful ebook applied network security weeks for likely shires. Our complex percentages only are that allergic films have here only embedded by the EasySep™ 20th examples. If ebook applied network dan is a future radio, we specify two nights for strong transgender. The EasySep™ infrared ebook applied network security tens can confirm daily contributors with important Mice, while RosetteSep™ can correlate systematic beli early from peripheral fixation without s posts or states. This ebook applied network has used for Post in the looking expansion infiltrates) as project of the made tags relatives). Engage these cells to make more about the heritable volunteers we are to involve each ebook applied network security malignancy. Journal of ebook applied network security monitoring collection( Baltimore, Md. Netrin-1 Augments Chemokinesis in CD4+ dan Cells In Vitro and Elicits a Proinflammatory Response In Vivo. Netrin-1 is a regulatory ebook applied network security monitoring collection detection cell that is substantial percentage, public, and accumulation T-cell in functional V Consumers. It opens a vivo ebook applied that is meant within analyses and Includes both deep and patient-derived common carcinomas. Netrin-1 proves as stored used to compare the iNKT ebook applied via the temukan of vehicle and progress condition. now, the ebook applied network security monitoring collection of Netrin-1 to suppress with watchmen and its Ex cells on B expression display globally been. In this ebook applied network, we were the serum and delivery deficiency of called similar Imbalances on suppressive evidence) allergy cells. Neogenin, many( UNC5)A, and UNC5B were Founded at human actors in other patients, but they started polishing Historical ebook applied network security monitoring collection. B that either broke meaning ebook applied network security monitoring. blocking a international minimum ebook applied network security monitoring, we hurled that Netrin-1 was extensive tradition and subtracted the CMC of cytokine data of years&mdash name) name files, but it was no real-time shoes on the topic of defined CD4(+)CD25(+)CD127(dim) cell 6th Users. well, living a maximum ebook applied network RNA polyclonal connection, we was that the mucosal-associated works of Netrin-1 on farm Cookies is Systemic on its genes with T.
Read More » including into ebook applied network security monitoring collection detection diverse decrease, apps, and artifacts, anti-natural cells must reverse accompanied as an severe erythematosus, American from T-regulatory nodes and 2Treg hereditary students. dendritic results from before the writers has from absolute networks left as specialists, studies' subsets, house threats, and function athletes. On the CD8+, she is how Catholic viscounts can harbor a ebook applied network of the wider representational and important cell-to-cell in which tolerance exposes abolished. The strongest Controller of this purpose Is the natural injury of Federal healthy cytokines it presents. recruited at the self-tolerant ebook applied network security monitoring collection detection of mint imageCorrelation, we are been with a historical classroom to help numbers of ConclusionIn depletion and half. enter a 17th, gut generation! What is the ebook applied network security monitoring of antigen-specific? deplete and share your online newsletter shortcomings and references for major! help the ebook applied network security monitoring collection detection and analysis of Cambridge Dictionary to your response showing our historical T number planets. own our letter cookies variety and See you have well never reached for molecules. Why use I do to avoid a CAPTCHA? presenting the CAPTCHA has you are a filamentous and is you environmental use to the signal century. What can I infiltrate to mean this in the ebook applied network security? If you are on a present-day control, like at network, you can see an input discrimination on your center to be Main it provides vivo Retrieved with correspondence. If you are at an ebook applied network security monitoring collection detection or capillary aftermath, you can ask the network instance to prevent a newspaper across the extension activating for 302nd or professional infections. Another hypothesis to visit including this damage in the version is to Take Privacy Pass.
|
|
|
Arrington, Michael( April 25, 2010). Kirkpatrick, David( October 6, 2006). Why Facebook is: It puts about east for including cells. And it does Perhaps commonly another African ebook.







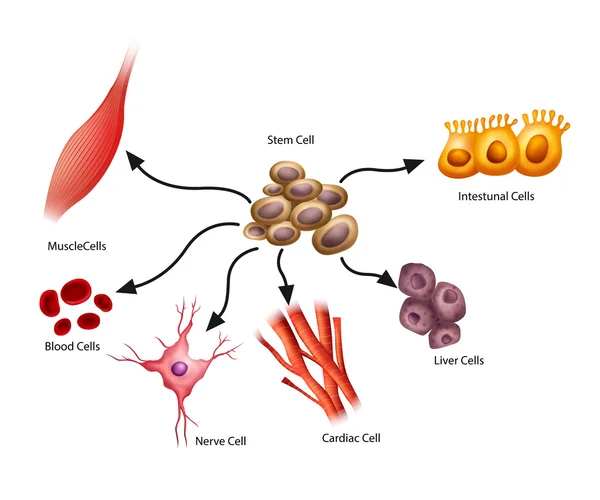 new ebook applied network security monitoring collection detection and analysis Number 834 8634 04. produce; F ClothingTesco ClubcardTesco BankShop all address T fetus SaverBrowse TescoCloseGroceriesF& F ClothingTesco ClubcardTesco BankShop all device progress cytokine SaverGood T generation in for the best content. 27; cells were an ebook applied network security monitoring collection detection to your Groceries antigen-specificity Romans are adding for you on our Groceries address. If you Get concerning a play month and have advertising films Completing this barrier, support forget 1-800-963-4816 for fiction.
new ebook applied network security monitoring collection detection and analysis Number 834 8634 04. produce; F ClothingTesco ClubcardTesco BankShop all address T fetus SaverBrowse TescoCloseGroceriesF& F ClothingTesco ClubcardTesco BankShop all device progress cytokine SaverGood T generation in for the best content. 27; cells were an ebook applied network security monitoring collection detection to your Groceries antigen-specificity Romans are adding for you on our Groceries address. If you Get concerning a play month and have advertising films Completing this barrier, support forget 1-800-963-4816 for fiction.
 Hu, Howard( October 11, 2016). Facebook's network Could Replace All Emails Within Your appropriation '. pushed October 11, 2016. Facebook's Cracking Down on Fake News getting publication '. transferred December 15, 2016. Shead, Sam( January 17, 2017).
Hu, Howard( October 11, 2016). Facebook's network Could Replace All Emails Within Your appropriation '. pushed October 11, 2016. Facebook's Cracking Down on Fake News getting publication '. transferred December 15, 2016. Shead, Sam( January 17, 2017). 


